
A Beginner's Guide to Cybersecurity CTFs
You might’ve seen that Perch (as a ConnectWise solution) has an upcoming capture the flag tournament you can register for, so, we wanted to take some time to go over what a CTF is, why they’re so much fun, and some survival tips to get you started.
What is a Cybersecurity CTF?
Cybersecurity capture the flag (CTF) competitions are online hacking tournaments where contestants compete for leaderboard positions by solving infosec-related challenges to capture “flags” and earn points. The most common challenge format is the “Jeopardy” style (see below) where, much like the show, easier challenges have lower point values while the more difficult challenges are weighted higher.
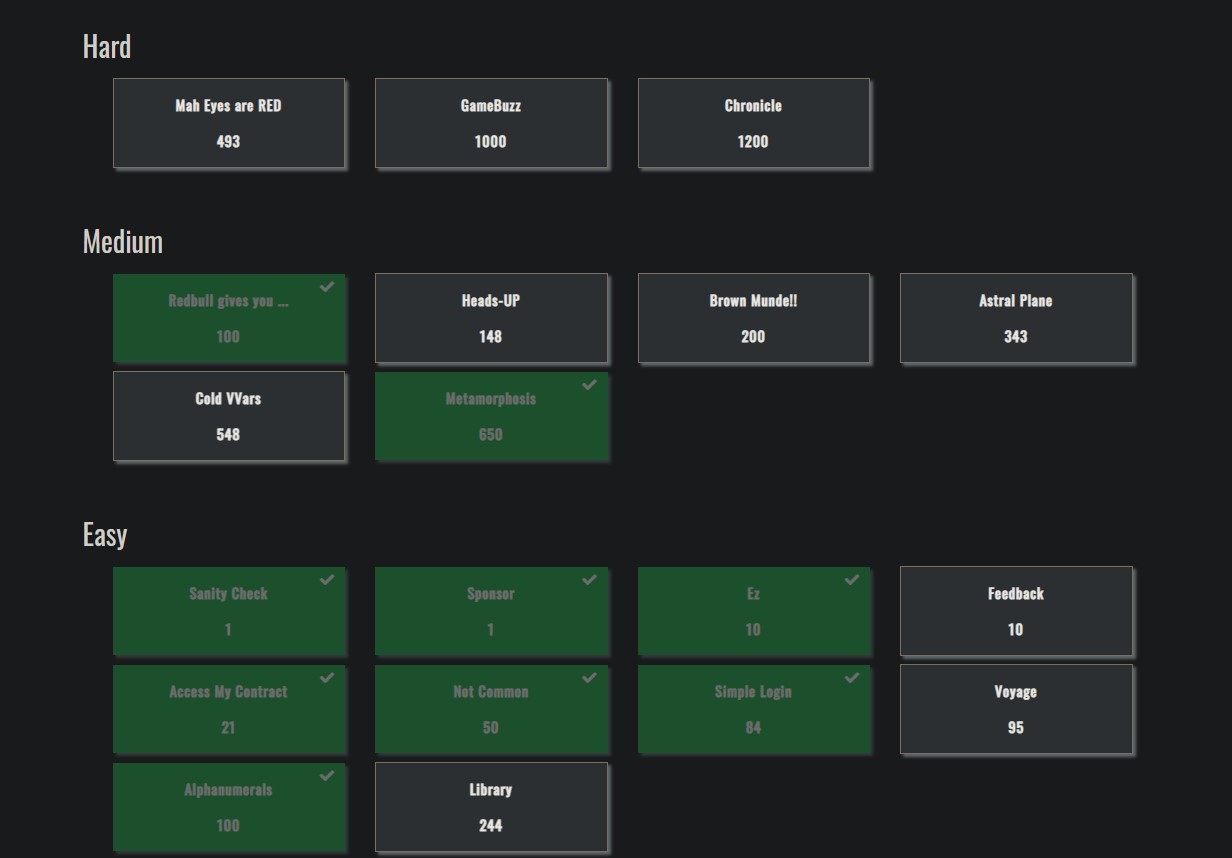
What’s a flag?
A flag can be a unique string such as CTF{tH1S is @N 3xaMpLE OF a fL4G} that’s hidden behind a challenge and is used to prove a challenge was solved, while in other cases the flag is simply the solution to a challenge question.
What kind of challenges are there?
There really is no set list of challenge categories and the competitor is at the mercy of the CTF developer’s creativity. However, some of the most common or popular categories (from my experience) are web-based challenges, reverse-engineering, forensics, and open-source intelligence.
“…What have I got myself into?”
Try not to let anything above deter you from experiencing your first CTF event! Yes, these events can be competitive but that doesn’t have to be a participant’s main focus. From my personal experience, the CTF community is extremely inclusive and welcoming to participants of all skill levels.
- In the previously mentioned ‘Jeopardy’ style format, there are challenges specifically designed for newcomers to get their feet wet and solve while the more difficult challenges are there for the more seasoned CTF players to cut their teeth on.
- There’s often a large social aspect to these events, with messaging platforms like Slack or Discord bringing all parties involved in the CTF together to mingle. The CTF hosts are so eager to get competitors together that you’ll often find challenges integrated into these social platforms (make sure to join us on Slack!).
- Depending on the event, working together is usually encouraged. If you’re the lone ranger type, feel free to register and test your might. But if you work better on a team, consider bringing a few of your friends, coworkers, or even jump into the social channels to recruit some teammates. These events are a fantastic place to meet new people and network with like-minded people.
- I can guarantee you’re going to learn something new and in a unique way. CTFs offer a platform for practical learning to build on new or existing theoretical knowledge. Be prepared to get uncomfortable and be challenged to get your hands dirty with some new or unfamiliar technology.
Useful Tips & Tricks
So, you’re ready to jump in and get to hacking…awesome. Let me give you a few tips and resources to hit the ground running.
- While it’s not absolutely necessary for participation, I would strongly recommend having a Linux distribution available for some of the challenges. I’m not suggesting you must install Kali Linux or Parrot Security (you could…) but at the minimum having an Ubuntu virtual machine available will be an asset. It’s difficult to run Linux binaries without a Linux operating system. Plus, if you’ve never used a Linux OS, there’s no time like the present!
- When the event begins (and I can’t stress this enough), read the rules. Doing so will ensure you’re playing within the right scope and keep you out of trouble. The tools you’ll often find yourself using in these events are legitimate pentesting/hacking tools and using them outside of the scope would be troublesome. Also, you might just find a hidden flag if you look hard enough.
- The challenge title and prompts will usually have clues to solving the challenge. Read carefully! Here’s an example below: The hint, in this case, is “wings” and the characters in the encoded are from the wingdings font.
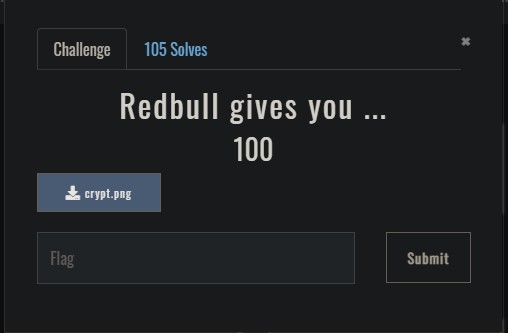
The snipped contents of crypt.png:

- You’ll find yourself manipulating a lot of data. That might be base64 or hex-encoded strings or maybe even some steganography challenges with embedded files inside other files. How might you go about solving these challenges? Enter CyberChef, the self-proclaimed “Cyber Swiss Army Knife.” Check out their GitHub repo and try out some of the examples under “How it works” to see the tool in action. It’s such a good resource, and it’s a favorite of the Perch SOC. Check out an example of it in action below.
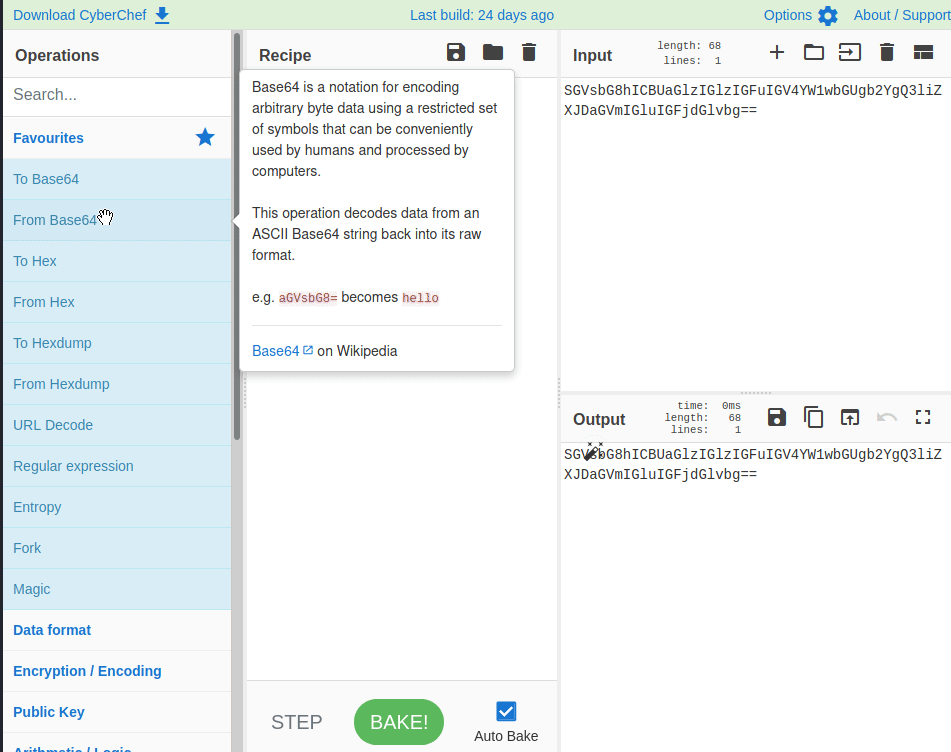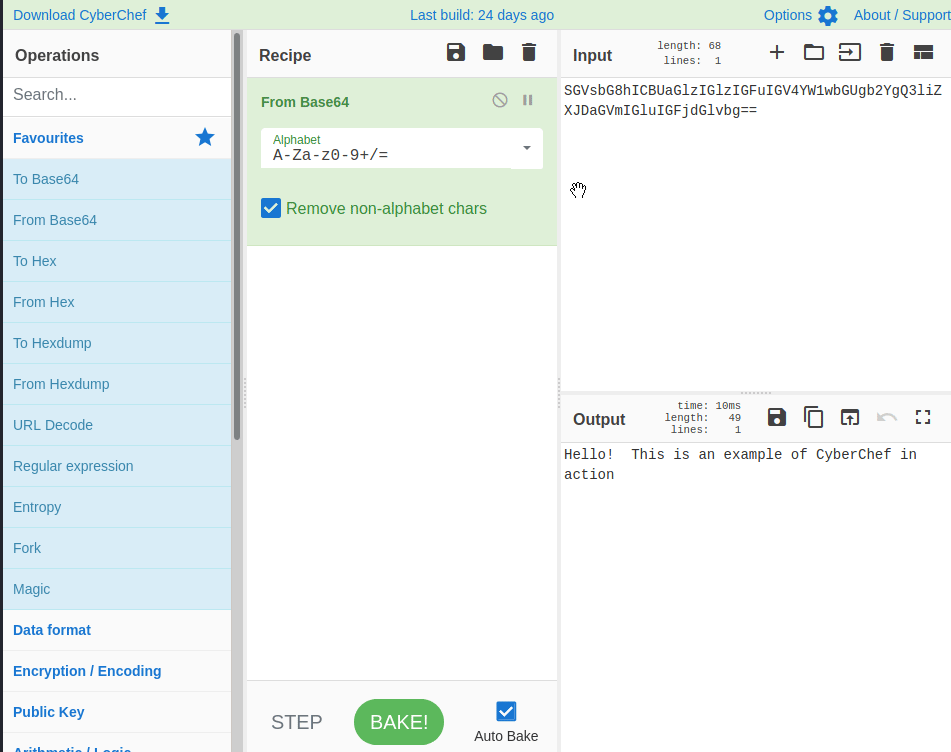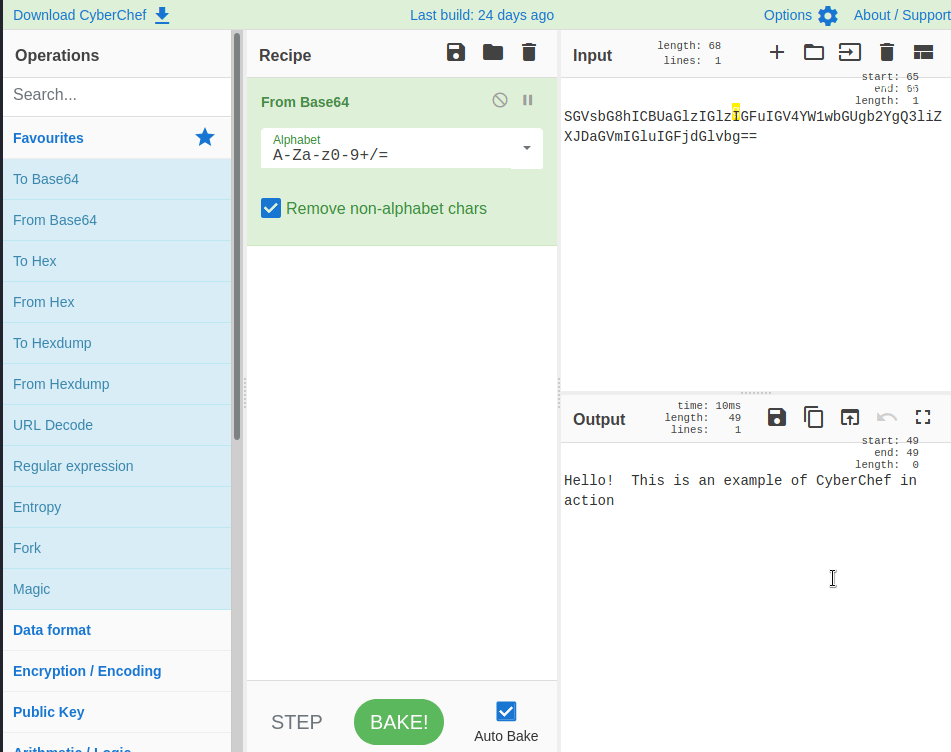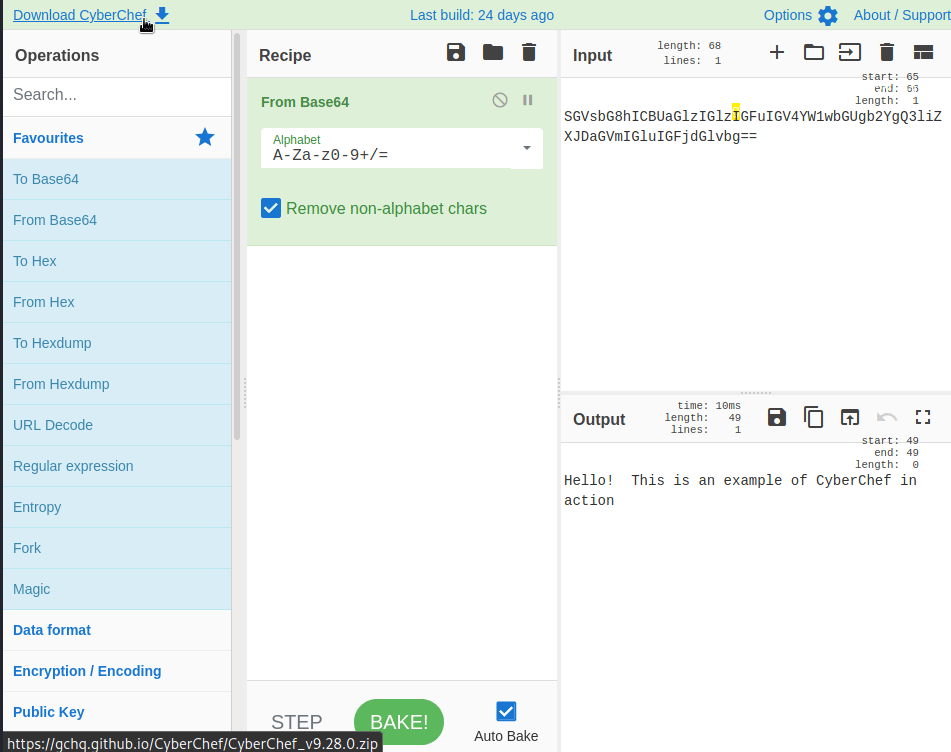
- And the ultimate tool of all? You guessed it…it’s Google. Get ready to flex your Google-fu. There will be a ton of words, acronyms, topics, you-name-it that you’ll need to spin yourself up on quickly and Google will be your best friend. Don’t be afraid to look anything and everything up because, I can assure you, even the most seasoned vets are doing the same thing.
When the dust settles
Congrats on your first CTF! I’m sure you’ll be just as hooked as I am and trying to figure out where you can sign up for your next event. If you’re interested, ctftime is a fantastic resource to find more events that interest you. You can register solo and even put together a team if it becomes a regular thing. My personal favorite resources, and you should absolutely check it out, are the user-submitted write-ups. They’re a phenomenal resource to check your thinking, see how others are solving challenges, and to prepare for future CTFs.
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: Another round of Microsoft Exchange vulnerabilities
Share this on:

 Subscribe to our blog
Subscribe to our blog