
A new ransomware gang on the block
A key component to protecting your systems is understanding the threat landscape. Part of that is keeping tabs on who the adversaries are and the tactics, techniques, and procedures they use.
At the end of last week (July 21), a new threat actor appeared with recruitment posts on two major Russian cybercrime forums.
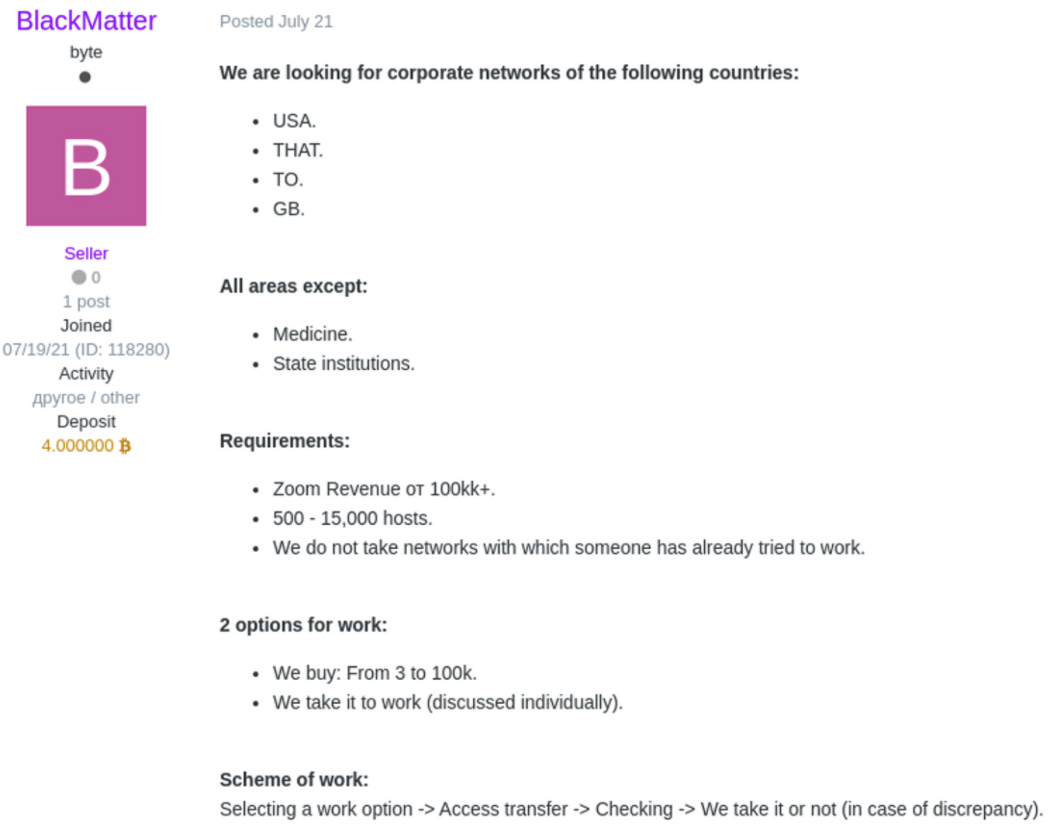
A user named “BlackMatter” with an account that joined the Exploit forum on July 19 made a post on July 21 offering between $3,000-$100,000 for access to corporate networks in the U.S., Canada, Australia, and the U.K. across all types of organizations, except for medical and State institutions. They listed additional requirements, such as how they are only interested in organizations with annual revenue greater than $100 million and 500-15,000 hosts. This user has also placed 4BTC (approximately $158,000 right now) into an escrow account on the Exploit forum, which is a good indication that they have significant resources available. A screenshot of the translated post can be seen below:
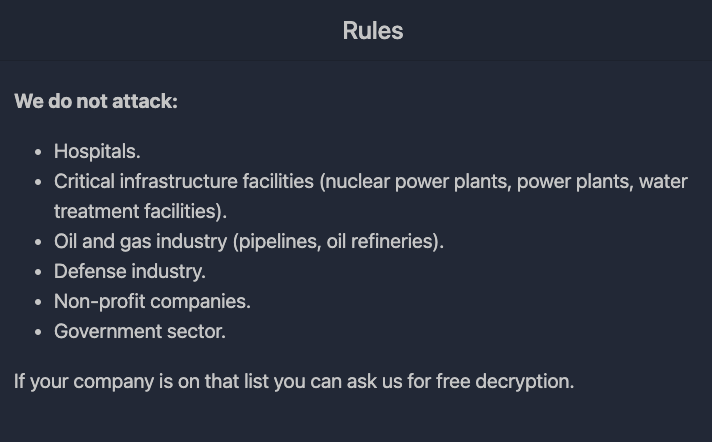
A new dark web leaks site was also launched this month titled “BlackMatter Ransomware” and is most likely tied to the BlackMatter user. According to their “About us” section, “We are a team that unites people according to one common interest - money.” Additionally, they list specific rules about organizations that are off-limits, very similar to the restrictions DarkSide put into place after the Colonial Pipeline hack before they shut down.
According to a report by Recorded Future, BlackMatter has claimed, “The project has incorporated in itself the best features of DarkSide, REvil, and LockBit.” This has led to confusing titles on articles across the internet as many media sources claim BlackMatter is REvil (a well-known Russian ransomware gang) rebranded. A REvil affiliate was responsible for the recent Kaseya Buffalo Jump ransomware attack, and after US President Joe Biden raised the issue with Vladimir Putin, they soon went dark. The REvil payment website and blog went offline, and their spokesperson Unkwn was removed from cybercrime forums. No one has heard from REvil since, which has led to many speculations, but at this time, no real information about REvil’s status is available.
So far, there is no evidence to support the claim that BlackMatter is REvil returned. As of right now, there is no indication that BlackMatter has performed any attacks yet, and as such, there are no samples of their ransomware to review. Some in the research community believe it is more likely that BlackMatter is DarkSide returned, but again, there is no evidence of this so far beyond the copied rules listed on their leaks site.
Ransomware groups come and go. Sometimes one will disappear for a while and come back with a new name. This is a fairly common practice to make tracking their activities more difficult and why it is not surprising if REvil or DarkSide returned. Recently, some other groups have rebranded. According to a recent tweet from @RansomAlert, SynACK (formerly FileLeaks) is now going by El-Cometa. A recent report from ZScaler suggests the new Grief ransomware is just a rebrand of DoppelPayer. There is also evidence that the new Haron ransomware gang, while probably not a rebrand, has some roots in the Avaddon and Thanos groups.
As the landscape of ransomware operators continues to change, the CRU will continue to keep watch and keep you informed.
ConnectWise CRU Collection in Perch
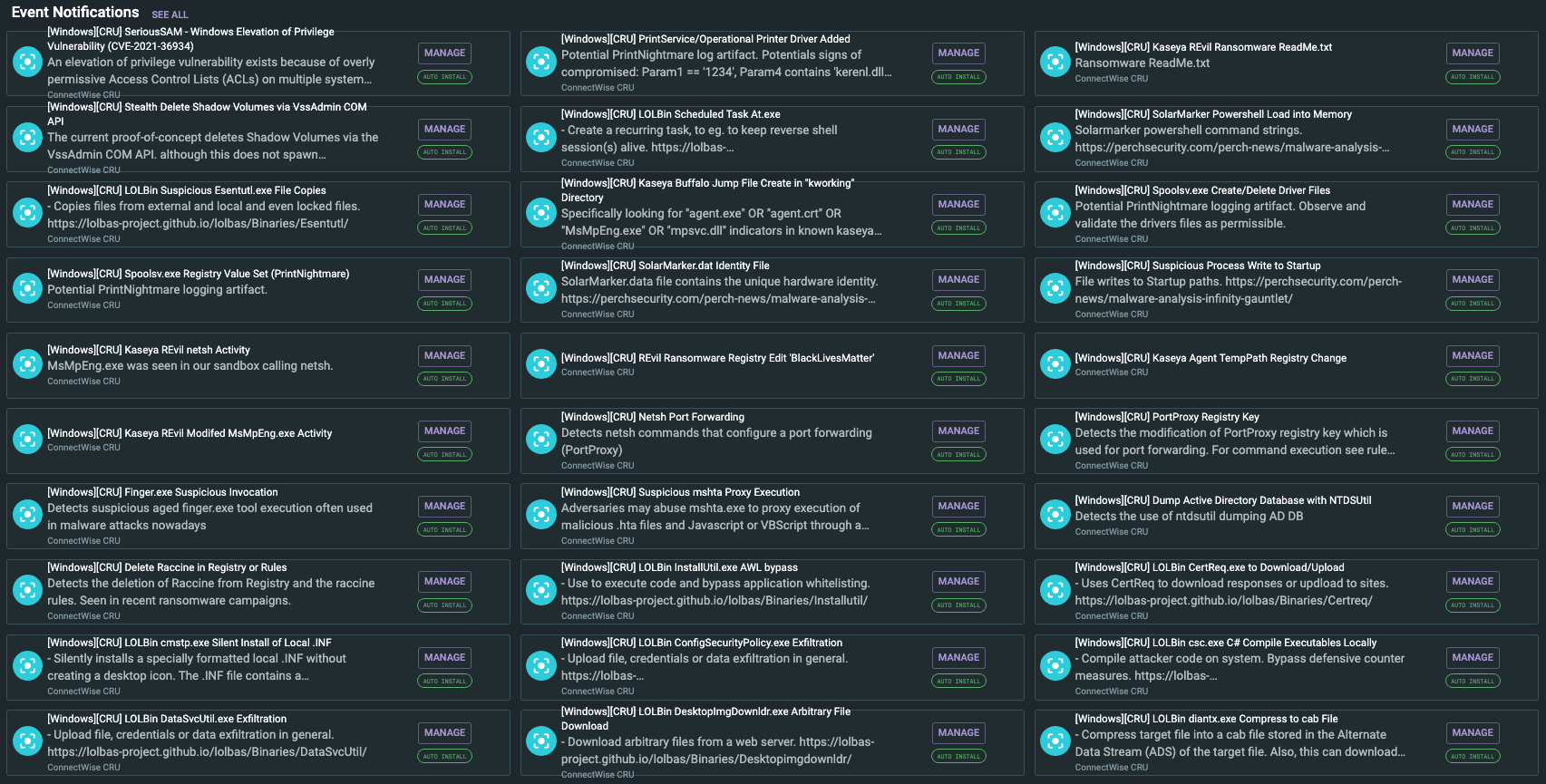
The ConnectWise CRU has been working tirelessly to improve threat detection in the Perch platform. As part of this effort, we have released a new ConnectWise CRU Collection in the Perch Marketplace with over 40 new Event Notifications for our SIEM customers. This collection includes detection for recent threats such as PrintNightmare and SeriousSAM/HiveNightmare. It also includes detection for several common methods of living-off-the-land binaries (LOLbins), which are methods for adversaries to use administrative tools built-in to your operating system to perform their tasks rather than “hack tools” or malware as well as several methods for detecting malicious PowerShell and more.
If you are a Perch partner and want to improve detection for these threats, we recommend you go to the Marketplace and install the ConnectWise CRU collection now.
- Bryson Medlock, the Dungeon Master
References
https://www.bankinfosecurity.com/revil-ransomware-operation-returning-as-blackmatter-a-17160
https://twitter.com/ransomalert/status/1420398550039605248?s=12
https://www.recordedfuture.com/blackmatter-ransomware-successor-darkside-revil/
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: The Print Nightmare just doesn’t stop
Share this on:
 Subscribe to our blog
Subscribe to our blog