
Cisco vulnerability runs wild
The usually weekly threat report is back again, and we’ve got an unpatched vulnerability to take note of, plus some sneaky action from malware operators. Check it out:
- Shlayer + Apple
- Cisco vuln running wild
- Emotet Red Dawn
- Busted: Egor Igorevich Kriuchkov v. Tesla
Apple opens the door for Shlayer
If you want to get your malware through Apple’s security controls, just ask them to approve it. On August 31, 2020, researchers announced that the Shlayer malware operators were abusing Apple’s automated notarizing process to land payloads.
If you’re not aware, Shlayer is a Mac malware variant first spotted in February 2018 targeting the macOS platform with a fake Adobe Flash Player installer.
Researcher Peter Dantini discovered Shlayer adware installers were being distributed through a malicious Homebrew website.
Since the adware was notarized, the installers could be executed on Mac devices running macOS Catalina without being blocked when launched.
The Shlayer operators used this method to deliver payloads to systems where the installers had been previously blocked.
Apple-focused security researcher Patrick Wardle confirmed that these installers delivered Shlayer adware samples notarized by Apple.
Upon execution, Shlayer installs the “mitmdump” proxy software and a trusted certificate to analyze and modify HTTPS traffic, allowing the malware to inject ads into web pages, monitor the victims’ browser traffic, and inject malicious scripts into visited sites.
Wardle stated that he reached out to Apple on August 28, 2020 to report the bug and Apple immediately revoked the certificates to prevent the Shlayer malware operators from spreading the adware.
Unpatched Cisco vulnerability runs wild
On August 29, 2020, Cisco released a security advisory regarding an actively exploited zero-day vulnerability that is associated with the Distance Vector Multicast Routing Protocol (DVMRP) feature that ships with the IOS XR version of the operating system.
The vulnerability is tracked as “CVE-2020-3566” and has been rated as “High” in severity with a CVSS score of 8.6. An unauthenticated attacker could exploit this vulnerability by sending crafted Internet Group Management Protocol (IGMP) traffic to exhaust the system’s memory and impact the running processes on the targeted device, leading to a denial of service (DoS).
Cisco’s Product Security Incident Response Team (PSIRT) identified on August 28, 2020 that the vulnerability was being actively exploited in the wild.
According to Cisco, the vulnerability affects any Cisco device running any version of the Cisco IOS XR software if active device interfaces are configured under multicast routing.
Organizations should disable multicast routing to prevent the risk of exploitation until Cisco releases an update for the vulnerability.
Emotet goes full Swayze in Red Dawn
On August 29, 2020, the Emotet botnet was observed by Joseph Roosen using a new template, tracked as “Red Dawn,” for their weaponized Word documents. Below, you can compare the old template (top) and new (bottom) template for Emotet maldocs.
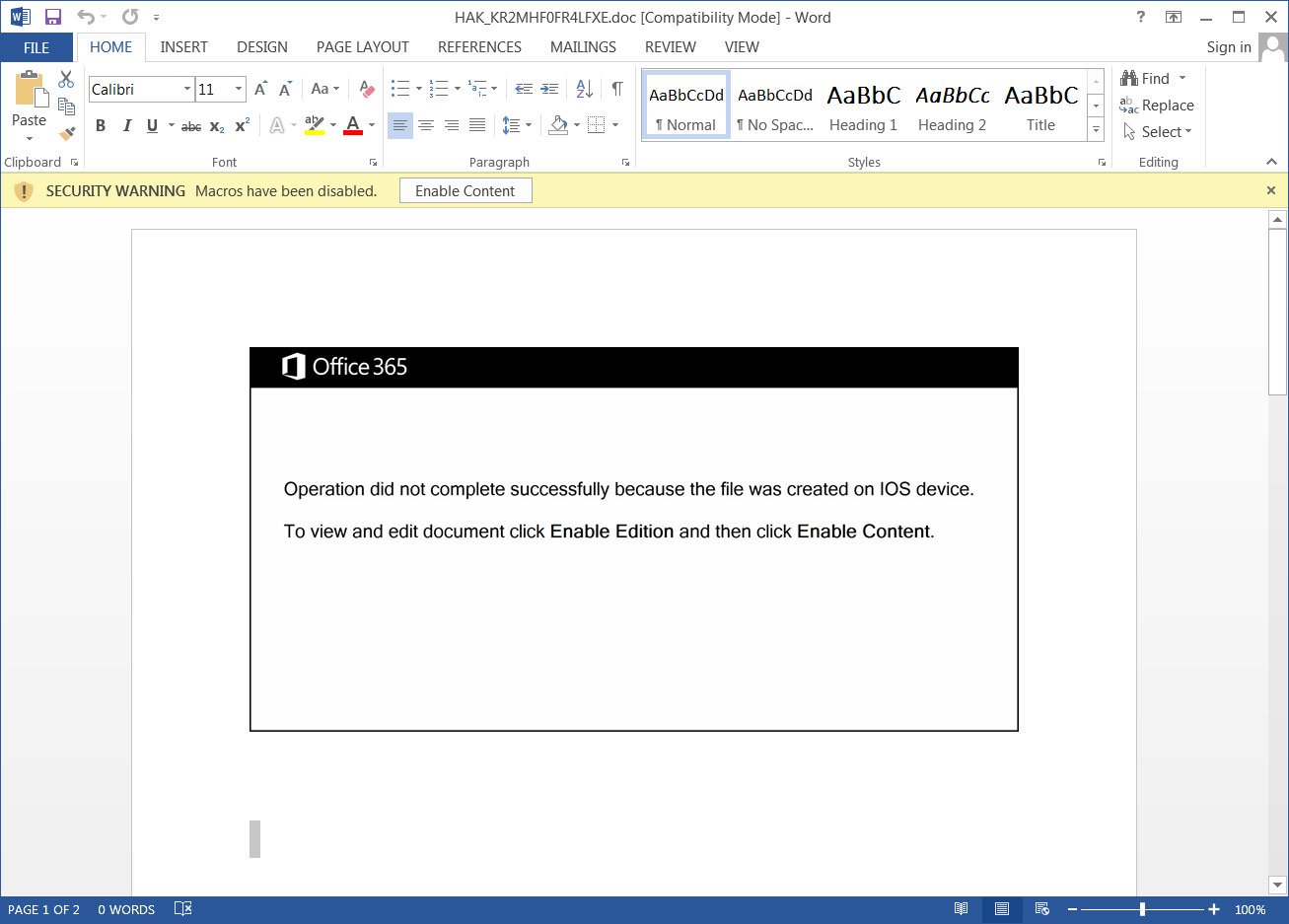
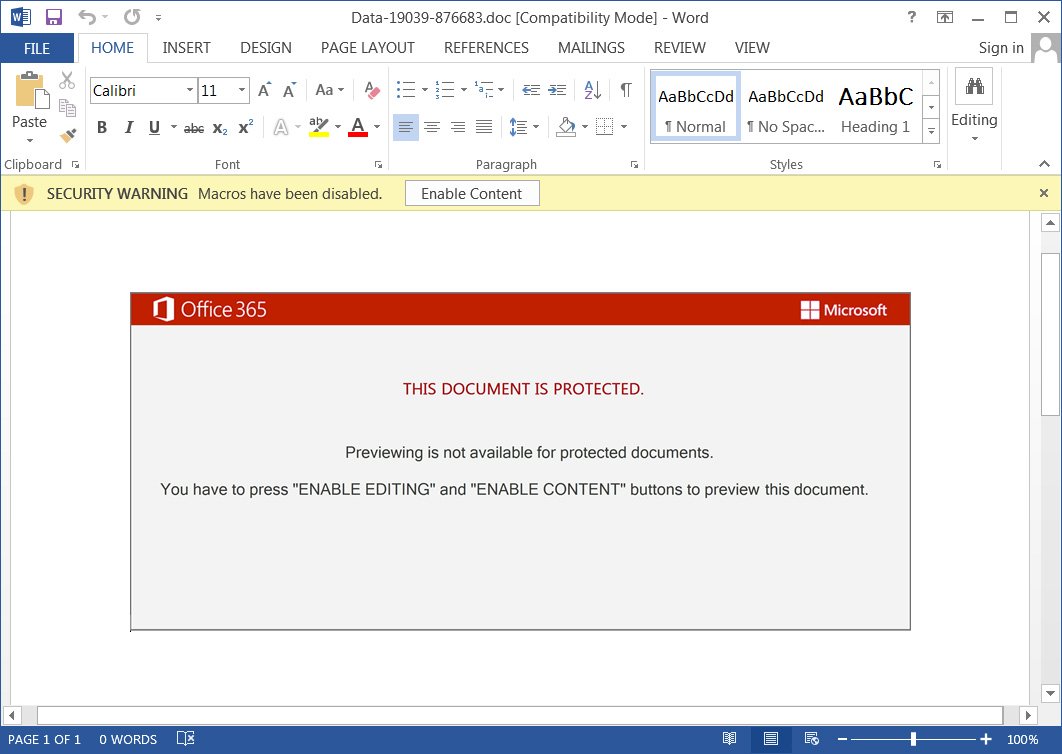 Images from Bleeping Computer
Images from Bleeping Computer
The Red Dawn template is different from templates used in previous campaigns due to the fact that it moves away from the iOS theme and shows users a message in red text that states “This document is protected” and instructions to enable macros.
Once the victim opens the attachment with macros enabled, malicious macros will be executed that will download and install the Emotet malware on the victim’s device.
These spam campaigns used malicious Word documents that were disguised as invoices, shipping information, COVID-19 information, resumes, financial documents, and scanned documents to entice victims into opening the malicious attachment.
Busted: Hacker charged in Tesla Ransomware Plot
On August 28, 2020, Tesla’s CEO, Elon Musk, confirmed that a Russian national named Egor Igorevich Kriuchkov attempted to recruit an employee of Tesla’s Nevada Gigafactory to plant malware on their network in exchange for $1 million USD.
According to court documents released by the US Department of Justice on August 25, 2020, Kriuchkov tried to convince the unnamed employee to deploy a custom-built malware strain onto the company’s network through a USB drive or via an email with an attachment that contained embedded malware.
The malware variant was not disclosed; however, the indictment stated that the malware could allow threat actors to steal sensitive data from the company’s network, which could be used to threaten Tesla with the release of the data unless Tesla paid a ransom demand.
Kriuchkov and his unnamed co-conspirators in Russia promised the Tesla employee payment in Bitcoins, after the successful deployment of malware.
Additionally, they had offered to launch a simultaneous Distributed Denial of Service (DDoS) attack on the company’s network to divert attention from the malware.
This has all the hallmarks of big game hunting. There is only one ransomware group that I’m aware of that coordinates DDoS with ransomware during the negotiation phases, and that’s Ako (a.k.a MedusaReborn). This alone isn’t enough to point the finger. Many DDoS services are available for a nominal fee.
The US Federal Bureau of Investigation (FBI) learned of the planned operation between July 15, 2020 and August 22, 2020 when Kriuchkov attempted to persuade the Tesla employee to act as an insider.
Kriuchkov was arrested and is facing a statutory maximum sentence of five years in prison and a charge of $250,000 if found guilty.
That’s all for this week, folks. Enjoy the unofficial last weekend of summer, and we’ll see you next time.
- Paul
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: Extortionware becomes the new norm
Share this on:
 Subscribe to our blog
Subscribe to our blog