
Customer Use Case: Mosaic Medical
Straight from the Nest
An intro from Perch
A powerful SIEM can be the difference you need in enhancing your security posture. The hatchling days of the Perch SIEM were limited to visualizing and searching a dashboard. We’ve been hard at work implementing requests from our users, making it easier to view everything you need to see in a single pane of glass.
Jason Shroeder, Network Security Specialist at Mosaic Medical, has joined us to show you how you can use Perch to cut through the noise and compile meaningful, actionable data to improve your security posture.
We’ve added integrations – particularly around SaaS – to get all your favorite tools in one place: Microsoft 365, G Suite, Bitdefender, AWS, Microsoft ATP, and more. Plus, you can create alerts and event notifications that can be triaged by our 24/7 SOC.
As workforces continue to go remote, these additions are key in helping you be proactive in your security posture.
Mosaic Medical, founded in 2002, is a “community-based, community-supported and community-governed network of community health centers that provide quality care for all regardless of life circumstances.” They’ve been using Perch since 2018.
Customer Use Case: Mosaic Medical
By: Jason Schroeder
We have seen a lot of benefits since adding Perch’s SIEM to our environment. The system has been great at ingesting log data and weeding it down to manageable pieces. On any given day, our systems may generate 8.5 million Windows log entries and 80,000 syslog entries. As we continue to increase the complexity of our logging environment, the utility of Perch’s SIEM grows. The importance of these logs isn’t in the logging itself, but in the Perch analysis.
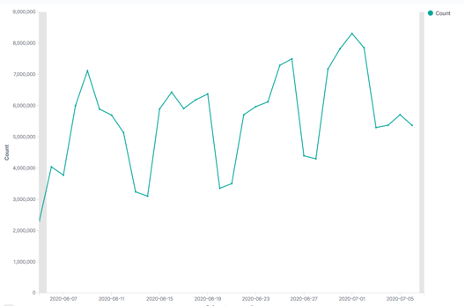
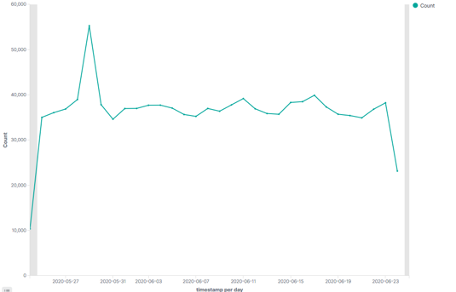
The built-in rule sets quickly cut through the noise to provide a clearer view of the items that are normal and those requiring further investigation. Visualization, automated reporting, and alerts generate meaningful data that speeds up identification and review of urgent issues.

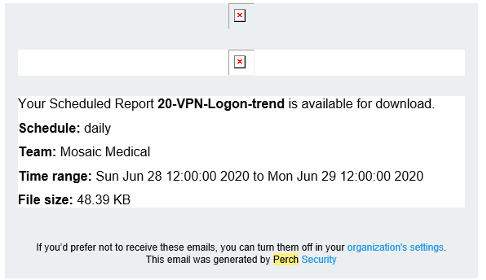
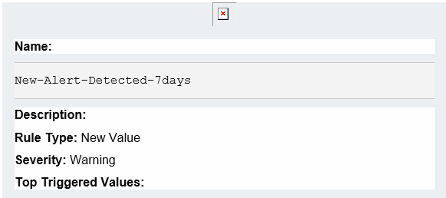
With the Perch SIEM, we can collect multiple log sources and data points in a single tool using common resources for search, data visualizations, alerting, and reporting. By unifying our varied log sources with flow data captured by the Perch sensor, we can look across data types to get a big-picture view of what is happening in our environment.
Investigations are quicker and more comprehensive and can help us identify and make proactive changes to our internal security configuration. One great success has been with data from Cylance Endpoint Protection Logs. Most days, Cylance will generate 800-1,000 syslog messages. Perch’s ruleset reduces that number to 20 log alerts for follow up. The investigation of these alerts can be done in minutes and trigger our incident response immediately.
As we shifted to remote work with the COVID-19 outbreak, we needed the ability to effectively remediate issues for our newly remote workforce. To support remote remediation and response, we pushed the installation of CYLANCEOPTICS to 246 laptops. This gave us the ability quickly isolate and lock down infected machines as a quick response to alert messages generated by the Perch SIEM.
Perch’s native integrations have grown since we first implemented the SIEM. As an organization, we have nearly completed our migration to Microsoft 365 (M365). Being able to monitor our M365 logs has been huge and helped ensure that our migration has been smooth and that we haven’t missed important alerts.
As we moved into Microsoft 365, we found changes in mail flow resulted in messages getting lost to Microsoft filters. Messages including critical vulnerability alerts, threat intelligence and IOCs, community security group communications, and others were being blocked. By creating daily reports with details of the Workload:ThreatIntelligence output, we were able to finetune M365 security settings to ensure that users did not miss important emails our rollout progressed.
Existing product integrations are also beginning to guide our purchasing decisions. Some of our traditional tools have had limited logging functionality and relied on portal access to look at what is going on. Perch makes my life easier with the integrations it supports, like Cisco Umbrella, Carbon Black, and Sentinel One. As a matter of fact, a clean integration with Perch is something that is on my mind when evaluating additional tools to incorporate at Mosaic.
Where to go from here
An outro from Perch
Today, it’s important to be proactive in your security posture, not reactive – especially with the new reality of a remote workforce. Being able to view your logs in a single pane of glass, cut through the noise, and visualize meaningful (and actionable) data is key to a strong security posture.
As Perch grows, we’re continuing to add integrations that work with the tools you already use, letting you see a detailed and holistic view within the Perch app.
Going through logs may seem daunting, but with the Perch app and our 24/7 SOC there to help you, it’s a task you can conquer.
See how you can make Perch work for you and your organization, right here.
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: Shifting gears: A cybersecurity journey for MSPs (Part 1)
Share this on:


 Subscribe to our blog
Subscribe to our blog