
Fake Kaseya updates serving up Cobalt Strike
Last week, we reported on a ransomware attack by REvil involving Kaseya’s RMM tool, VSA, that affected between 40-60 MSPs and over 1,000 organizations. This week, we’re seeing other threat actors try to capitalize on REvil’s success with a malspam campaign disguised as a Kaseya VSA security update.
@MBThreatIntel was the first to report on this Tuesday afternoon of this week. The malicious email claims to contain an update from Microsoft to fix a vulnerability with an attached file named “SecurityUpdates.exe” and a link supposedly to Kaseya’s website.
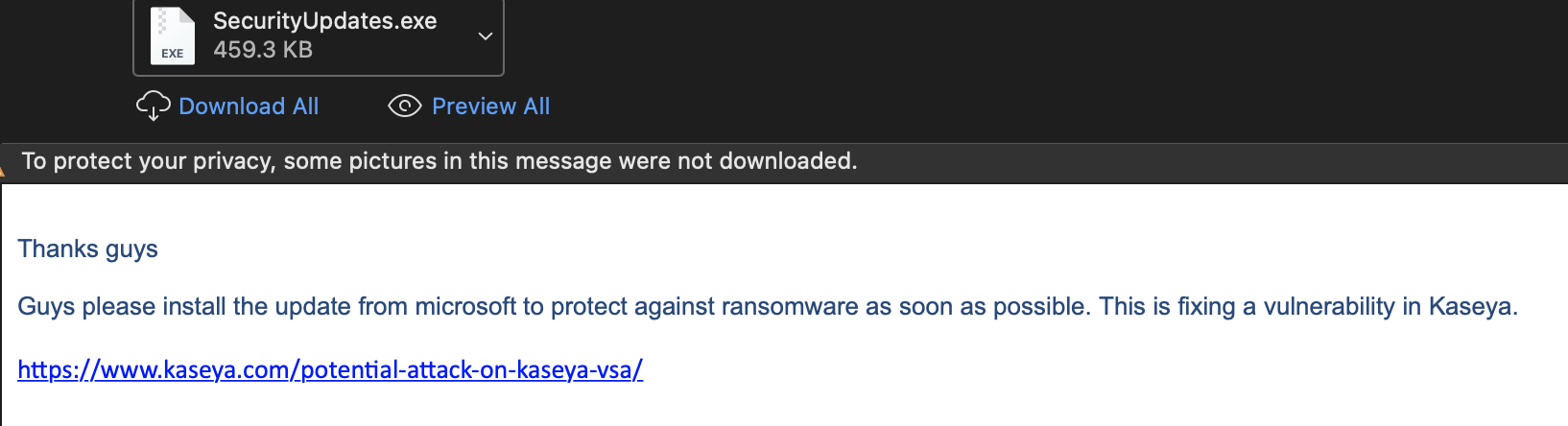
The file attachment is actually a Cobalt Strike payload, and the link (disguised as an official Kaseya page) leads to another Cobalt Strike payload. Cobalt Strike is an adversary simulation tool designed for red team operations but is often used for some command and control (C2) activity by malicious actors. We saw similar activity a month ago after the Colonial Pipeline incident where threat actors were targeting organizations with spam claiming to contain updates to protect their systems that actually contained Cobalt Strike.
Here at the CRU, we have been hunting for any signs of customers that may have been affected by this malspam campaign. We’ve seen a few of our partners targeted with this malicious email but their users have been smart enough not to run the malicious payload.
Babuk is back
Back in May, we reported on an announcement by threat actor group Babuk that they were handing off their source code to another group and would be dropping out of the ransomware gang, focusing on data exfiltration and extortion instead. Babuk is a fairly newer group that first became known at the beginning of 2021 and claims to have begun targeting companies in mid-October 2020. They are perhaps best known for ransoming Washington DC’s Metropolitan Police Department.
At the end of June, a tool was leaked that was used by Babuk to create custom ransomware. There was a spike in Babuk ransom incidents starting on June 29th after the release of this tool. This new actor using the leaked tool was only after a small change, in one instance only asking for .006 BTC (~$200) instead of the hundreds of thousands or millions of dollars the normal Babuk gang sought. Since that time, the Babuk gang itself has made it known that the older version of their tool was leaked, but they have a new version that they still use for corporate networks.
- Bryson Medlock, the Dungeon Master
References
https://cyware.com/news/babuk-ransomware-is-back-in-action-9f4e2e11
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: A Nightmare on Spooler Street
Share this on:

 Subscribe to our blog
Subscribe to our blog