M&A: Why Can’t Cybersecurity Get No Respect?
Buying things. It’s the American way, isn’t it? It’s also something near and dear to my heart. Except when I buy something, I don’t usually spend hundreds of millions of dollars or more. However, in the world of mergers and acquisitions (M&A), this is exactly what happens.
I know what you’re thinking: what does M&A have to do with cybersecurity? At Perch, we have the opportunity to help acquiring organizations through the M&A process. M&A is often filled with various legal, contractual, and compliance issues, and we’ve noticed that cybersecurity is becoming a critical piece that must be considered equally throughout the entire process.
But let me get back to the buying: there’s no Amazon-style return policy if you get it wrong. I can’t put my nice shiny M&A deal back into a box and send it off for a return. Or can I?
Believe it or not, this can (and does) happen quite frequently in an M&A deal. See, these M&A opportunities are unpredictable and fraught with volatility. Everything needs to be perfect for an M&A to go through. At least that’s what the lawyers are always telling me (wait…maybe those lawyers are just trying to pad their pockets with additional billable hours?).
The missing sink
Let’s take a look at exactly how detailed an M&A process can be. The image below is from our friends at Corporate Finance Institute (imagine if we changed the Perch name to Corporate Cybersecurity Institute! I bet that’d go over well as a discussion starter at the next speed dating event.)
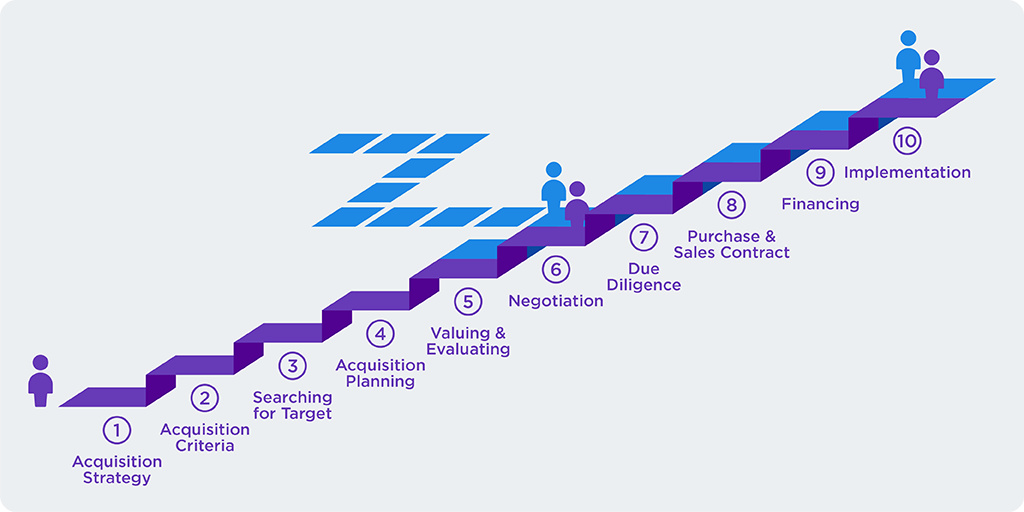
Source: https://corporatefinanceinstitute.com/resources/knowledge/deals/mergers-acquisitions-ma-process/
Looking at this process, these ten steps are enough to put just about anybody to sleep. While each step could be a dissertation of its own, let’s focus on the one that’s a critically vital mountain to overcome for the success of an M&A: Step 7 — Due Diligence. If ever there’s a step that leads to more failed M&As, due diligence is it.
If you look at most classic due diligence processes in M&A, it usually revolves around things like financial metrics, corporate structure, and litigation. You know, the boring stuff. Take a look at this well-known (and pretty darn exhaustive) due diligence checklist.
It’s got everything except the kitchen sink. And that missing sink — cybersecurity — is a doozie. How is it that the due diligence process so often misses a critical step that can lead to disastrous post-M&A results?
Pin the tail on the breach
First things first: is cybersecurity really critical? I’d argue strongly that it is! Gartner (I can’t get no CISO respect without quoting these guys) says that by 2022, 60% of organizations will consider cybersecurity as a critical factor in M&A activity.
Personally, I want to know who the other 40% are that don’t. Now what’s really interesting is when you read between the lines, only 5% of organizations from that survey reported cybersecurity as critical. Wow.
So, what happens when we don’t treat cybersecurity as critical in M&A? The deal closes, the press releases are produced, the stock price jumps, and the investors are happy. Until it gets reported weeks later that the company had a breach. And that breach cost millions in losses from a drop in stock value on top of all the rest of the typical reputational and regulatory damages.
And where did that breach first occur? In the M&A process. The organization being acquired already had an active threat actor embedded in the network, and no one noticed until it was too late. In trying times like this, the lawyers come rushing to the rescue — but mostly to point fingers at one another and, as ever, continuing to ramp up those billable hours in the ever-fun game of pin the tail on the donkey breach.
Wes’ 5 nifty steps
So, how can we ensure that cybersecurity is included in the M&A process? How can we reduce the likelihood of a breach wreaking havoc in the M&A process? Here’s my nifty 5-step process:
-
Eat your own dog food
If your organization doesn’t already take cybersecurity seriously, you’re only compounding your risk by getting active in M&A. How can you ensure the acquired organization is secure if yours isn’t? It’s the definition of a risky proposition and the blind leading blind. While maturing your cybersecurity program is beyond the scope of this blog post, I’d recommend mapping your security program to a framework like the NIST CSF and ensure you have buy-in from the board on down. -
Lead with risk
Every M&A process should be led with risk throughout the entire journey. This certainly includes cybersecurity in due diligence. This risk assessment process could (and often should!) have third-party assistance. I’ve discovered that third-party auditors are often able to uncover issues and areas of note because they have a fresh eye. So, include risk assessments and treat their results seriously. -
Give it time
If your board wants M&A deals to close in just a few months, you have a problem. Most M&A due diligence processes take six months to a year, and sometimes longer. It’s never fun, but it’s better to get it right than deal with the damages of a breach. The Gartner study mentioned earlier says the same: only 36% of organizations feel like they were given enough time to review cybersecurity standards and processes for the acquired organization. That’s scary. -
Don’t forget the technical controls
While we lead with risk in the M&A process, don’t forget technical controls review. This is where issues can often be brought to light that otherwise will never shine. This should always include vulnerability scanning (to determine patching cadence and hygiene) and penetration testing. But there’s one more thing that organizations often leave out. While vulnerability scanning and pen testing can reveal weaknesses in systems, they cannot determine if a threat actor has already compromised the network.Perch has a number of Fortune 500 companies that use our platform for exactly this purpose. Because Perch performs threat detection and response, we have the unique ability in the M&A process to review and determine any persistent threat activity that otherwise might never be found until after the M&A is complete.
-
Include cybersecurity earlier in the M&A process
If you have to start somewhere, you always need to include cybersecurity during due diligence. It’s the minimum. But if you can include cybersecurity earlier in the process, all the better. For example, cybersecurity could be included in step 1 (acquisition strategy) of the M&A process to set the standard. It could be included in step 2 (specific criteria) and so forth. The most mature cyber-enabled M&A processes include cybersecurity in every step of the process.
While cybersecurity is always going to be a higher risk item in M&A, following these items tightly and expanding upon them will lead to more successful M&A activity, maintaining shareholder value, and keeping yourself from the ever-present threat of a resume-generating event. Perch has helped many organizations through this process, and we’d love for you to lean on our experience.
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: How Perch helps you tackle Microsoft 365 log fatigue
Share this on:



 Subscribe to our blog
Subscribe to our blog