
Ransomware dominates 2020
What a crazy week it’s been in the cybersecurity world. There’s really only one story this week: more ransomware-related incidents that are dominating the headlines.
- Microsoft published its Digital Defense Report
- UHS v. Ryuk
- CMA CGM v. Ragnar Locker
- Swatch v. ???
Digital Defense Report
Microsoft released the Digital Defense Report today, which reinforced many of the conclusions and predictions we made in our 2020 Security Report.
Ransomware has dominated the news this year, with exfiltration and extortion tactics driving the number of incidents that we know about.
By Microsoft’s accounting, “Over 70% of human-operated ransomware attacks in the past year originated with Remote Desktop Protocol (RDP) brute force.”
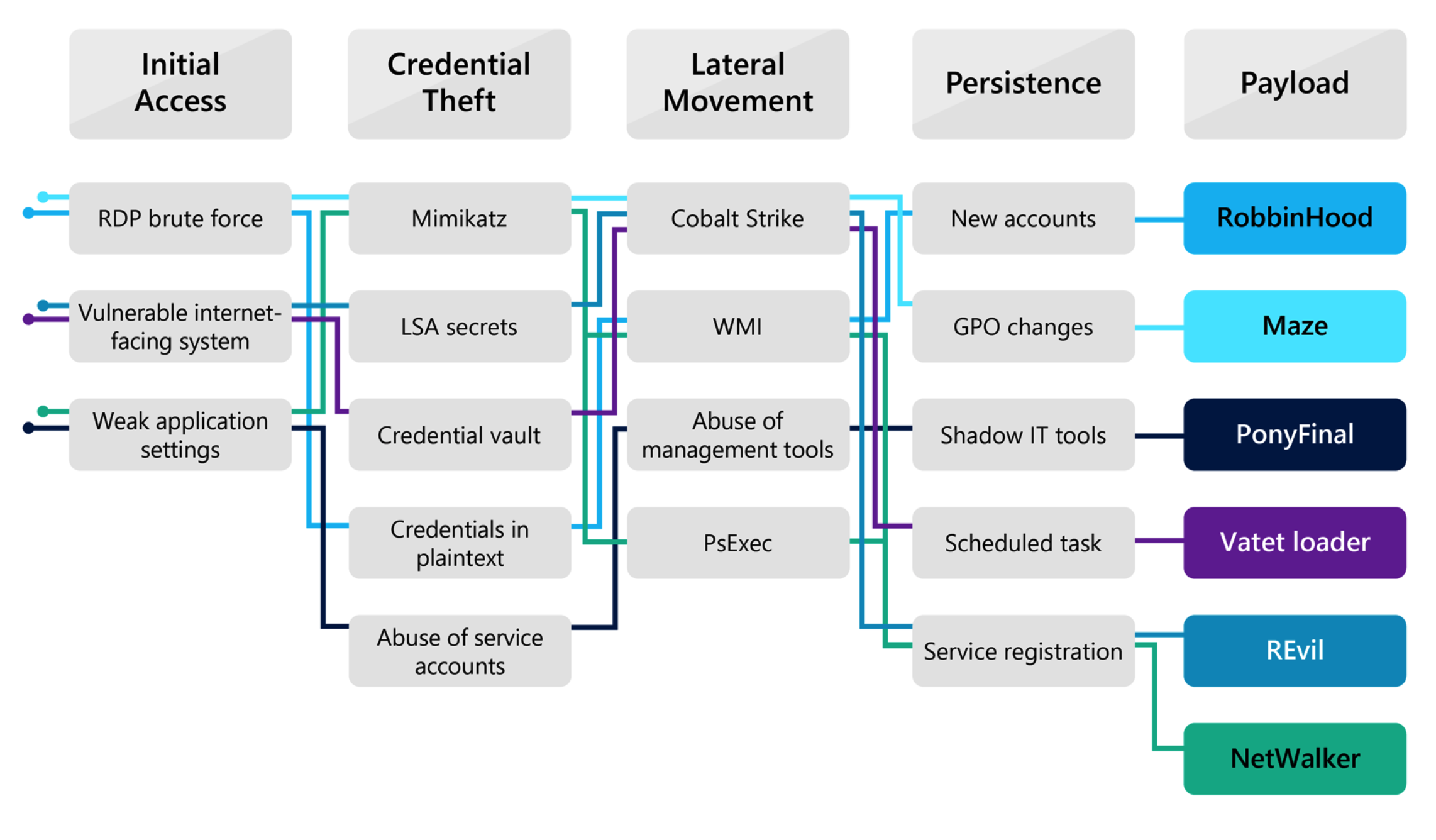
Image from Microsoft’s Digital Defense Report
Microsoft noted that time to encryption is shrinking, “In some instances, cybercriminals went from initial entry to ransoming the entire network in less than 45 minutes.” To evade detection, ransomware operators disable preventative security controls within an organization. However, there are still opportunities to detect and respond to their initial access, lateral movement, and persistence mechanisms before your systems are encrypted.
Additionally, many of these top strains are exfiltrating data for additional extortion. Maze, REvil, and NetWalker all exfiltrate and leak victim data on their ransomware leak sites.
UHS v. Ryuk
Over the weekend of September 26, 2020, Universal Health Services (UHS) suffered from an incident involving Ryuk ransomware.
According to employees and patients reporting on social media platforms, the incident took place on September 27 at around 2:00 am CT. Internal IT systems have not been in operation since Sunday morning local time.
Some patients were even reportedly turned away and redirected to other hospitals after UHS facilities were unable to carry out lab work.
Employees shared publicly that computers rebooted and then showed a ransom note on the screen. Computers were then shut down, and IT staff asked hospital personnel to keep systems offline.
According to a Reddit thread, similar IT issues were reported in Arizona, Florida, and California.
UHS is one of the largest healthcare providers in the U.S., with more than 400 hospitals across the US and the UK.
CMA CGM v Ragnar Locker
French shipping giant CMA CGM S.A. suffered from an incident involving Ragnar Locker ransomware that brought down customer services.
The ransomware first encrypted the company’s offices in China over the weekend. How far it then spread across CMA CGM’s network isn’t clear, but the company’s main website was offline for some time and CMA CGM staff in Europe have been told not to use any company tech equipment.
When the website partially returned, it displayed a security notice that reads, “We have decided to temporarily suspend all access to our e-commerce sites to protect our customers,” along with a statement that all communications were secure and that maritime and port operations are functioning as normal.
In a statement Monday, CMA CGM describes a cyberattack “impacting peripheral servers” with access to applications interrupted to “prevent the malware from spreading.”
CMA CGM employees have shared a ransom note from Ragnar Locker mentioning CMA CGM by name. This shows that CMA CGM wasn’t a random target, but they were explicitly targeted.
Swatch v. ???
In similar news that’s still evolving, Swiss watchmaker Swatch Group shut down its IT systems over the weekend after identifying a cyberattack targeting its organization.
Swatch Group, a Swiss watchmaker known for its colorful watches, employs over 36,000 people with $9.6 billion in revenue for 2019.
“Swatch Group immediately assessed and analyzed the nature of the attack, took appropriate measures, and implemented the necessary corrections. The situation will return to normal as soon as possible,” they said in a statement to BleepingComputer.
Swatch Group wouldn’t elaborate further about the type of attack they suffered, but Bleeping Computer suggested it was likely a ransomware attack.
This sounds like a case of Swatch spotting the indicators of compromise in time to respond before data could be encrypted. This Swatch story could be the light at the end of the tunnel showing its possible to prevent ransomware outbreaks by monitoring your network and logs for indicators of compromise.
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: Are you ready for Zerologon?
Share this on:
 Subscribe to our blog
Subscribe to our blog