
RMM Buffalo Jumping – Independence Day Remix
What do we know?
Today’s cybersecurity landscape is complex and yet, simple at the same time. Vendors, partners, end users – we are all in this together, and the goal is to protect the larger community from bad actors. ConnectWise shares many mutual partners with other vendors in our space, and we do not want to see any vendor compromised. With that, it is important to understand what has happened in the past 36+ hours and what that means to the community. Here is our take.
Kaseya, a software company that builds IT Management tools for MSPs, has a long history of serving the MSP community and working with us here at ConnectWise. Kaseya was compromised and used to spread Sodinokibi (aka REvil) Ransomware through their on-prem VSA appliance. According to Kaseya, around 40 MSPs have had their VSA appliances compromised, which REvil then used as a platform for a Buffalo Jump to target their clients, reaching as many as 1,000 small-to-medium sized businesses , including Swedish grocery retailer Coop, forcing them to close 800 stores on Saturday. REvil is the same Ransomware-as-a-Service Russian cybercrime gang linked to the JBS meat processor attack in May and as we noted a couple of weeks ago has been particularly busy over the past month, targeting energy companies and even a US nuclear weapons contractor. Kaseya will release more details of the zero-day vulnerability after a patch is released as mentioned by Kevin Beaumont in his article.
According to the REvil operators, the ransom is $45k per encrypted device. REvil uses four types of public/private key pairs; one for the operator, a campaign key pair, a system-specific key pair generated when the system gets encrypted (encrypted with both the operator and campaign public keys and stored in each encrypted file and ransom note), and then a new key pair generated for each encrypted file with the public key stored in each encrypted file. The system and file keys are used to generate a Salsa20 key that is used to encrypt the file.
Huntress and Blackpoint led the community through the initial findings of the incident and reported the details of the incident to Reddit.
False Sense of Security
@fwosar shared details of the configuration for the Kaseya REvil sample here. The C2 domains were looking like extra juicy IoCs, but further down in the configuration file we see the “net” flag being set to false, which instructed the ransomware to not create any network traffic.
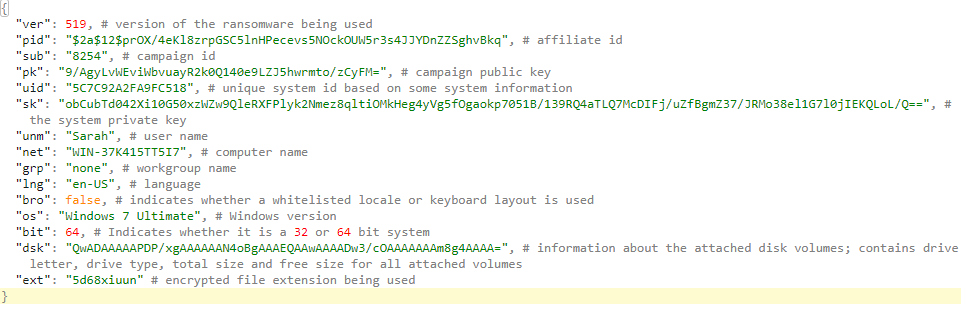
@fwosar also shared details of the key that is generated post infection and presented in the ransom Readme text. This key is used at the payment site to load the ransom page for the compromised device. The key contains several points of information that include info about the campaign the device was compromised by, user info, and computer info. Details that may contribute to ransom demands.
Leak Site Updates
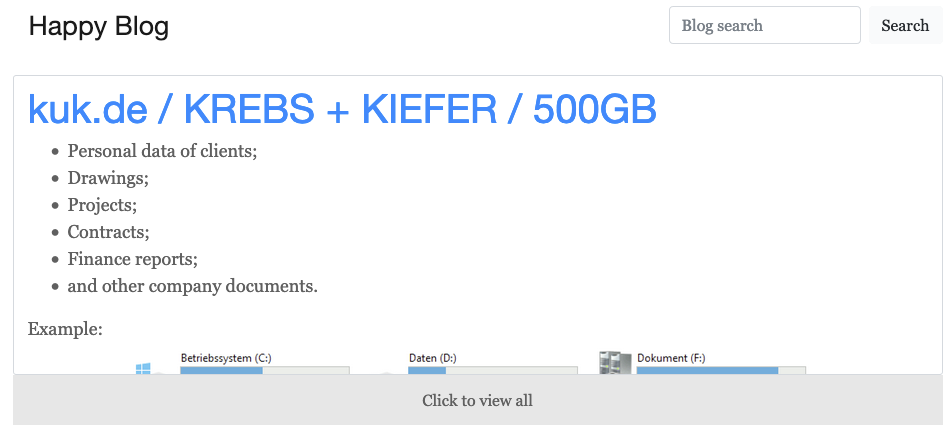
Since the Kaseya incident, there has only been one leak added to REvil leak site though we would not be surprised to see new leaks coming out in the next few weeks. There is no clear indication that “kuk.de” was compromised through Kaseya. We will continue to monitor the blog site for any new additions.
Look into our Sandbox
The ConnectWise CRU acquired a copy of the malware sample being distributed and ran it through our internal sandbox built on top of the Perch platform and found the following:
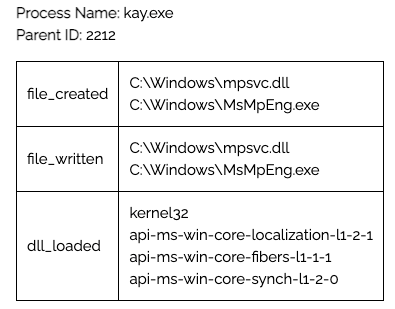
- Initial sample creating fake
MsMpEng.exeandmpsvc.dllin a static directoryC:\Windows
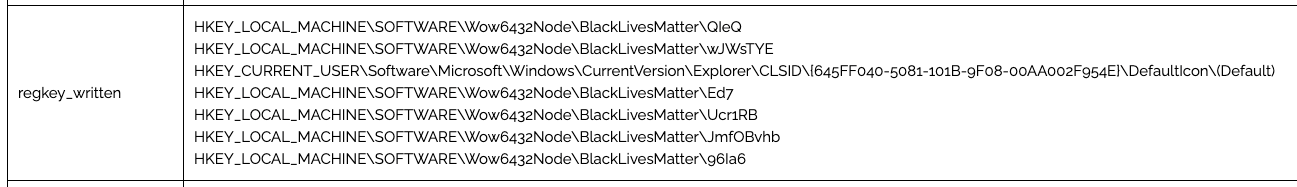
- Inserting Values into Registry.
- Enabling Network Discovery on the device.

- Enumerating All Shadow Copies on a Computer
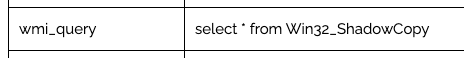
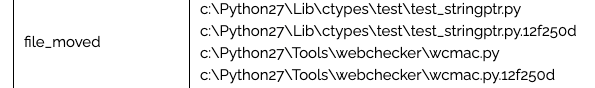
- Encrypting files with the extension
.12f250d. A new file extension is generated for each host
- Ransom note generated in each directory with encrypted files,
12f250d-readme.txt. Filename is based on the generated file extension:
file - {'name': '12f250d-readme.txt', 'path': 'C:\\Users\\User\\Desktop\\RoAMer\\.git\\logs\\refs\\remotes\\origin\\12f250d-readme.txt', 'directory': 'C:\\Users\\User\\Desktop\\RoAMer\\.git\\logs\\refs\\remotes\\origin', 'extension': 'txt'}
Windows Logging Detection
The CRU has outlined the following SIEM queries to identify any malicious activity.
File Creations for known file drops.
Sysmon Event ID: 11 AND TargetFilename contains "kworking\agent.exe" OR "kworking\agent.crt" OR "Windows\MsMpEng.exe" OR "Windows\mpsvc.dll" OR "windows\cert.exe"
Registry Add/Delete
Sysmon Event ID: (12 OR 13) AND TargetObject contains "SOFTWARE\Wow6432Node\BlackLivesMatter"
File Signatures
Sysmon Event ID: 7 AND Signature contains "PB03 TRANSPORT LTD." OR "BUKTBAI, OOO" OR "OOO Saylent" OR "OOO Reliz" OR "OOO Dibies"
Suspicious MsMgEng.exe
Sysmon Event ID: * AND Image contains "MsMpEng.exe" AND NOT IN ("C:\ProgramData\Microsoft\Windows Defender\" OR "C:\Program Files\Windows Defender" OR "C:\Program Files\Microsoft Security Client"
ConnectWise/Perch Detection:
The CRU has added logging detection within the Perch platform for the activity mentioned above. Subscribe to SIEM alerts under the Marketplace/Windows Advanced (Beta).
[Windows][CRU] Kaseya Buffalo Jump File Create in “kworking” Directory
[Windows][CRU] Kaseya REvil Ransomware ReadMe.txt
[Windows][CRU] Kaseya REvil netsh Activity
[Windows][CRU] REvil Ransomware Registry Edit ‘BlackLivesMatter’
[Windows][CRU] Kaseya REvil File Signature Issuer
Authors
- Stuart Gonzalez
- Bryson Medlock
- Ross Farington
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: Galaxy Ransomware begins affiliate program
Share this on:
 Subscribe to our blog
Subscribe to our blog