
See, everybody needs security
This week, we’re covering updates to SolarWinds, an increase in data auctions, PUP ransomware, and a phishing campaign that got hit. You’ll see a recurring theme: everybody needs cybersecurity (even the baddies!). Let’s get started.
SolarWinds update
The recent SolarWinds supply-chain attack has been at the top of the security news feeds for weeks now, and this week is no exception. Previously high-target tech companies such as SolarWinds, Microsoft, and FireEye reported breaches by the same threat actor, and CrowdStrike reported a failed breach attempt. This week, cybersecurity firm Malwarebytes reported that the threat actor behind the SolarWinds supply-chain attack also targeted their organization.
According to Malwarebytes, their software is safe to use. Unlike the supply-chain attack that targeted the SolarWinds build system, the threat actor only gained access to a limited subset of internal emails.
This threat actor – believed to be a nation-state – has been notoriously hard to track down and, in many cases, remained in control of compromised systems for over a year. Microsoft has performed an in-depth analysis of this threat actor’s behavior and came up with a list of evasion techniques used. Overall, the actor meticulously planned and executed every step necessary to evade detection:
- Methodic avoidance of shared indicators for each compromised host by deploying DLL implants custom compiled for each target using the free, open-source adversary simulation software, Cobalt
- Camouflage and blending into the environment by renaming tools and binaries to match files and programs on the compromised device
- Disabling event logging using Auditpol before hands-on keyboard activity and re-enabling afterward
- Creating firewall rules to minimize outgoing packets for certain protocols before running noisy network enumeration activities (then removing after these operations were completed)
- Carefully planning lateral movement activities by first disabling security services on targeted hosts
- They are also believed to have used timestomping to change artifacts’ timestamps and leveraged wiping procedures and tools to hinder malicious DLL implants discovery in affected environments.
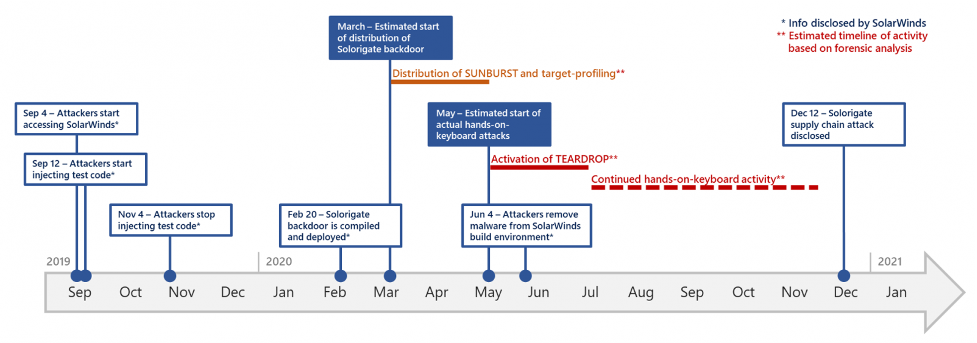
Microsoft also released a timeline of events, as shown above. This event continues to show us what a well-funded, determined threat actor can accomplish. While the group’s identity behind these attacks is still unconfirmed, Kaspersky has found some tie with the Russian Turla hacking group after finding that the Sunburst backdoor shares source code with the Kazuar backdoor, and federal sources believe this to be a Russian APT.
Auctions everywhere
There have been several threat actors selling access to data via auction on various exploit forums this week. While not unusual, there do seem to be more than usual.
Here’s a look at the significant RDP access up for sale:
One user, ‘trillion,’ is auctioning away network access to a U.S. water treatment company. According to their post, trillion found RDP credentials when looking through their botnet logs. The auction starts at $1k, but trillion will give immediate access for $3k.
Another user, ‘barf,’ on another exploit forum had several listings. Some of these auctions have been concluded, and a few are still ongoing:
- A plumbing supply company in the United Kingdom (U.K.)
- A U.K. exporter of the education services
- A German company with $5 million in annual revenue
- A Peruvian organization that sells chemicals
- A Peruvian fruit exporter
- A U.S. equipment supplier
- An Australian manufacturer
- An Australian processor of plastic and cardboard
- An Italian organization that specializes in the treatment of hazardous waste
- A city hall in Spain
- A German organization that specializes in metal structure manufacturing
The threat actor going by ‘corp’ on the forum snagged up most of these auctions, with a couple going to ‘FloodService’ and one each for ‘samson’ and ‘Jaffar.’
On another top-tier exploit forum, the user ‘babam’ sold RDP access of an undisclosed U.S. company to an unknown buyer. The organization is said to be a supplier of technologies and services for the energy sector with $1 billion in annual revenue and 1,000 employees.
‘IGhostI,’ a member of another forum, is selling access to a server of an unnamed Canadian company. According to the threat actor, there is sensitive data available on the server that includes bank accounts with all passwords, social media advertisement accounts with passwords, employee data, corporate credit card information, and other data.
‘JohnFlint,’ a member of the forum Exploit, is auctioning web shell access to a major unspecified Spanish cannabis forum with 431,000 users. The auction starts at $300 for access to the database, including usernames and passwords.
Auctions for leaked data are prevalent this week as well, including leaked data from the WHO, the European Space Agency, major global companies, and various sports organizations by an actor known as ‘mont4na.’ A database containing compromised data on military-related personnel (Ministries of Defense, soldiers, and contractors) from unspecified nations in South America is for sale by an actor going by ‘WICK1.’
Many of these auctions are for leaked RDP access. Perch regularly monitors for unusual RDP access and alerts customers when we see someone using RDP from unusual places. We also strongly recommend to our customers that you lock down RDP behind a firewall. Even if credentials are leaked, threat actors cannot use that information to establish a foothold in your organization.
From PUP to ransom
Potentially Unwanted Programs (PUPs) are programs that users may install intentionally but are still unwanted because they often contain adware and spyware. Typically, these come in the form of small, free applications that are supposed to solve a problem that often doesn’t exist. For example, there are countless “Registry Cleaners” that you can install that are nothing more than vaporware.
This week, we saw the real threat these PUPs can cause.
On January 18, 2021, IObit, a Chinese software company that produces system optimization and security applications for Microsoft Windows operating systems, such as “Driver Booster” or “Uninstaller” (both PUPs), was reportedly compromised by unknown threat actors who distributed the DeroHE ransomware variant to IObit forum members.
Members of the IObit forum began receiving emails stating members of the forum were entitled to a 1-year free license of their software. The email contained a “GET IT NOW” button that directed victims to a forums[.]iobit[.].com URL, and distributed a file named free-iobit-license-promo.zip. This file contained an “IObit License Manager” with an embedded malicious DLL. When the file is executed, it installs DeroHE ransomware to “C:\Program Files (x86)\IObit\iobit.dll” and then installed a Windows autorun named “IObit License Manager” which executes “rundll32 “C:\Program Files (x86)\IObit\iobit.dll”,DllEntry” at every logon.
The ransomware then displays a message box to prevent victims from shutting down their devices while the ransomware is working. When encrypting files, the ransomware will append the “.DeroHE” extension to the encrypted files. Additionally, the ransomware will create two files: one named “FILES_ENCRYPTED.html,” which contains a list of all encrypted files, and the other named “READ_TO_DECRYPT.html,” which is the ransom note.
The ransom note contains two payment options to retrieve the compromised files. The first option is that IObit can send 100,000 DERO coins (cryptocurrency) or approximately $100,000 to get a decryption key for all compromised victims’ machines. The second option states that IObit users can send 200 DERO coins or approximately $100 to the provided address to decrypt their machine.
The threat actor likely compromised IObit’s forum and gained access to an administrative account by injecting a malicious script on forum pages.
Perch recommends using standard industry-approved controls, such as limiting software installation to admins and removing local admin privileges, to reduce risks such as the one presented by PUPS. While the PUP itself is at best benign, we can see here that the risk is beyond the PUP itself, and in this case, the trust established with existing users was targeted.
Bad guys need security, too
An ongoing massive phishing campaign was itself compromised this week. Cyber research companies Check Point and OTORIO were following a massive phishing campaign that has targeted thousands of organizations worldwide. The attackers used previously compromised email accounts to send their phishing emails to help keep the campaign undetected. Related activity for this actor goes back to May 2020.
The phishing emails came in different shapes and sizes, but all included an HTML attachment, appearing to be a delivery of a Xerox scan notification. When opening the attachment, a target is presented with a Microsoft 365 login page. If they entered their credentials, the username and password are reported back to one of several compromised WordPress sites.
In a report released on January 21, the two research companies tracking this activity explained that the data acquired by this threat actor was saved in publicly available files that were indexed by Google. As a result, stolen email addresses and passwords were available. The data they collected determined that companies in the construction, energy, and I.T. sectors were the most prevalent targets.
See, everybody needs security…even the bad guys.
-
Bryson Medlock
Senior Threat Researcher
The Dungeon Master
Sources:
- https://www.bleepingcomputer.com/news/security/hacker-blunder-leaves-stolen-passwords-exposed-via-google-search/
- https://www.bleepingcomputer.com/news/security/microsoft-shares-how-solarwinds-hackers-evaded-detection/
- https://www.bleepingcomputer.com/news/security/malwarebytes-says-solarwinds-hackers-accessed-its-internal-emails/
- https://www.bleepingcomputer.com/news/security/iobit-forums-hacked-to-spread-ransomware-to-its-members/
- https://www.bleepingcomputer.com/news/security/us-govt-says-russian-state-hackers-likely-behind-solarwinds-hack/
- https://www.bleepingcomputer.com/news/security/sunburst-backdoor-shares-features-with-russian-apt-malware/
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: SUNSPOT malware spotted in SolarWinds
Share this on:
 Subscribe to our blog
Subscribe to our blog