
The ransomware roller coaster
Back in April, we told you about new scare tactics being used by the Cl0p ransomware group. Cl0p has been very active in 2021, specifically targeting vulnerabilities in Accellion FTA that were patched in December 2020 and January 2021. This group has been active since at least 2019 and is believed to be responsible for approximately $500 million in financial damages.
Last week, Ukrainian law enforcement arrested six suspects believed to be associated with Cl0p. According to a press statement from Wednesday of last week, the Cyberpolice of Ukraine was involved in an international operation involving law enforcement authorities from South Korea, the US, and Interpol that conducted searches in 21 homes in the capital city of Kiev (Kyiv) and surrounding area. A video of the takedown shows officials seizing computers, around $185,000 in cash, and several cars – including a Tesla and Mercedes. Authorities also claim to have seized control of servers used by the ransomware group and shut down their infrastructure.
However, the roller coaster doesn’t end there. Even with these arrests, it seems as though Cl0p is still active. According to @darktracer_int, they just announced a new victim today.
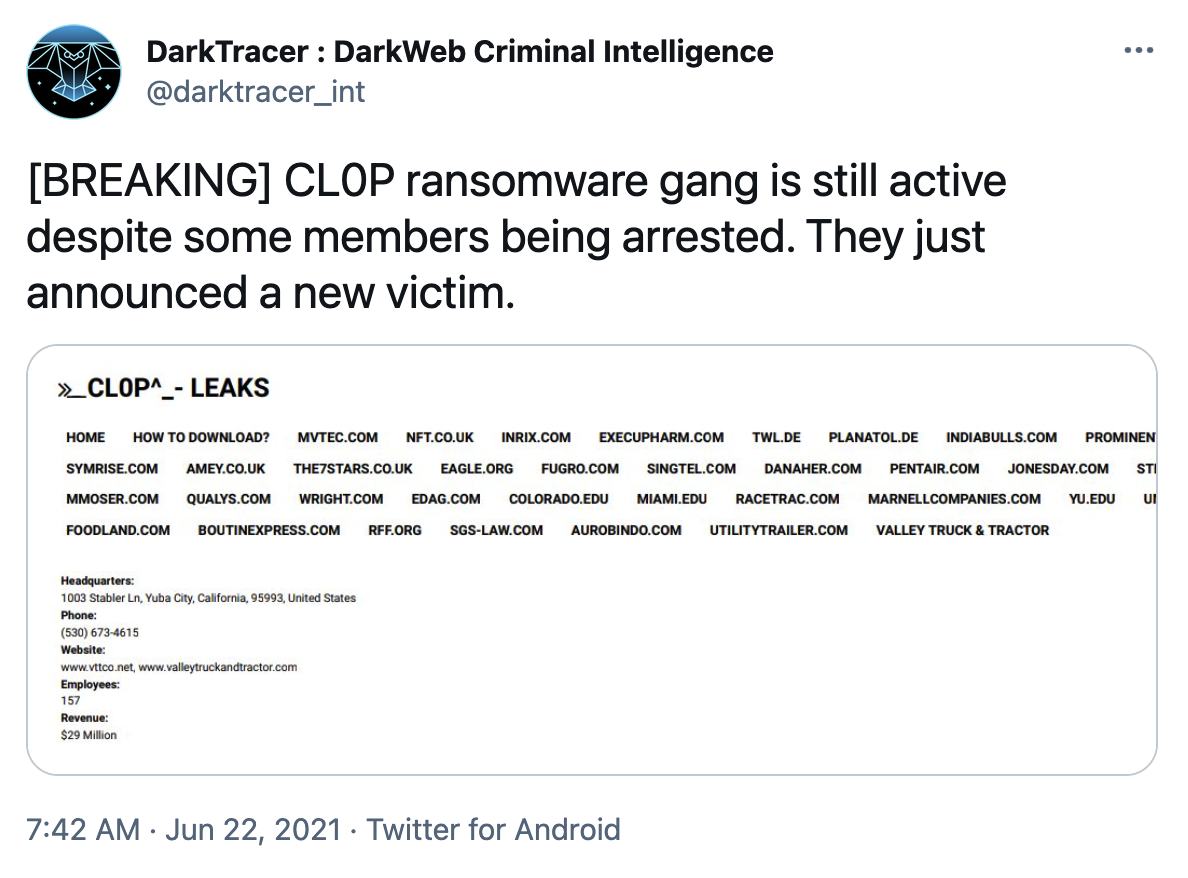
This year has seen multiple takedowns of various malicious groups, beginning with the takedown of the Netwalker ransomware group and the infamous Emotet botnet-as-a-service at the beginning of the year.
We’ve also seen a string of ransomware groups giving up the game this year, beginning with FonixCrypter at the beginning of the year and, more recently, the group behind Avaddon ransomware shut down operations and released decryption keys for all their victims.
There have been several big wins for the good guys this year, but life isn’t all Perchy. Despite these wins, ransomware attacks are still on the rise. Latest data suggests there are over 7 ransomware attacks PER HOUR in the US alone. We’ve begun seeing ransomware attacks affecting more than just their targets, such as the Colonial Pipeline and JBS hacks we’ve discussed before.
REvil in particular has been busy. Last week, REvil was attributed to ransomware and data theft attacks targeting Invenergy, a multinational renewable energy company headquartered in Chicago. Perhaps even more concerning is the alleged ransom and data theft of US nuclear weapons contractor Sol Oriens. REvil is auctioning off what they claim to have stolen from Sol Oriens and have posted on their data leaks site images of hiring documents, payroll documents, and wage reports. There is nothing to indicate anything other than HR data was stolen, but REvil has put the pressure on threatening to share “relevant documentation and data to military angencies (sic) of our choise (sic).”

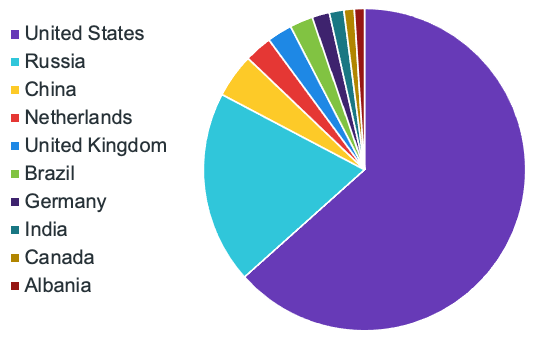
In response to these ever-growing threats, President Biden issued several Executive Orders last month, and last week met with Russian President Vladimir Putin at their first in-person summit in Geneva, Switzerland on Wednesday. According to our own data we’ve collected from the Perch app, around 20% of all malicious traffic that we have seen targeting our customers over the past 90 days originated from Russia. It is commonly believed in the intelligence community that Russia is a safe haven for bad actors who target US-based organizations. During the summit, Putin denied these allegations.
According to President Biden, “I talked about the proposition that certain critical infrastructure should be off-limits to attack. Period. By cyber or any other means. I gave them a list, 16 specific entities. 16 defined as critical infrastructure.” This week’s meeting follows a stern warning that was sent out by the US and other G7 countries on Monday that specifically called out Russia for either launching their own cyberattacks or harboring ransomware organizations.
All that being said, we’ve had some big wins this year, but ransomware is the biggest cybersecurity threat right now and the threat is only getting worse.
- Bryson Medlock, the Dungeon Master
References
https://beta.darkreading.com/attacks-breaches/ukraine-police-disrupt-cl0p-ransomware-operation
https://krebsonsecurity.com/2021/06/ukrainian-police-nab-six-tied-to-clop-ransomware/
https://therecord.media/avaddon-ransomware-operation-shuts-down-and-releases-decryption-keys/
https://www.bleepingcomputer.com/news/security/revil-ransomware-hits-us-nuclear-weapons-contractor/
https://www.zdnet.com/article/biden-and-putin-spar-over-cybersecurity-ransomware-at-geneva-summit/
We'd love to hear your thoughts. Find us on Twitter, LinkedIn or write in to hello@perchsecurity.com
Next: VMWare exploit being used in the wild
Share this on:
 Subscribe to our blog
Subscribe to our blog